
Microsoft has announced that it will automatically enable stricter secure default settings known as 'security defaults' on all existing Azure Active Directory (Azure AD) tenants in late June 2022.
First introduced in October 2019 only for new tenants, security defaults are a set of basic security mechanisms designed to introduce good identity security hygiene with a minimum of effort, even for organizations that don't have an IT team.
Two months later, in January 2020, Microsoft announced that security defaults already had been enabled for 60,000 new tenants.
After more than two years, over 30 million organizations are now protected by security defaults that enforce multifactor authentication (MFA) and modern authentication requirements.
"We are delighted with the success of this program, but tenants created before October 2019 were not included in security defaults and were vulnerable unless they explicitly enabled features like Conditional Access, Identity Protection, and MFA," said Alex Weinert, Director of Identity Security at Microsoft.
"That's why we're so excited to announce the rollout of security defaults to existing tenants, targeting those who haven't changed any security settings since deployment.
"When complete, this rollout will protect an additional 60 million accounts (roughly the population of the United Kingdom!) from the most common identity attacks."
Security defaults to secure user accounts
After the rollout starts, Global administrators will be notified and can either enable security defaults or snooze their enforcement for 14 days when they will be toggled on automatically.
Once toggled on in an Azure AD tenant, users will be required to register for MFA within 14 days using the Microsoft Authenticator app, with Global admins also asked to provide a phone number.
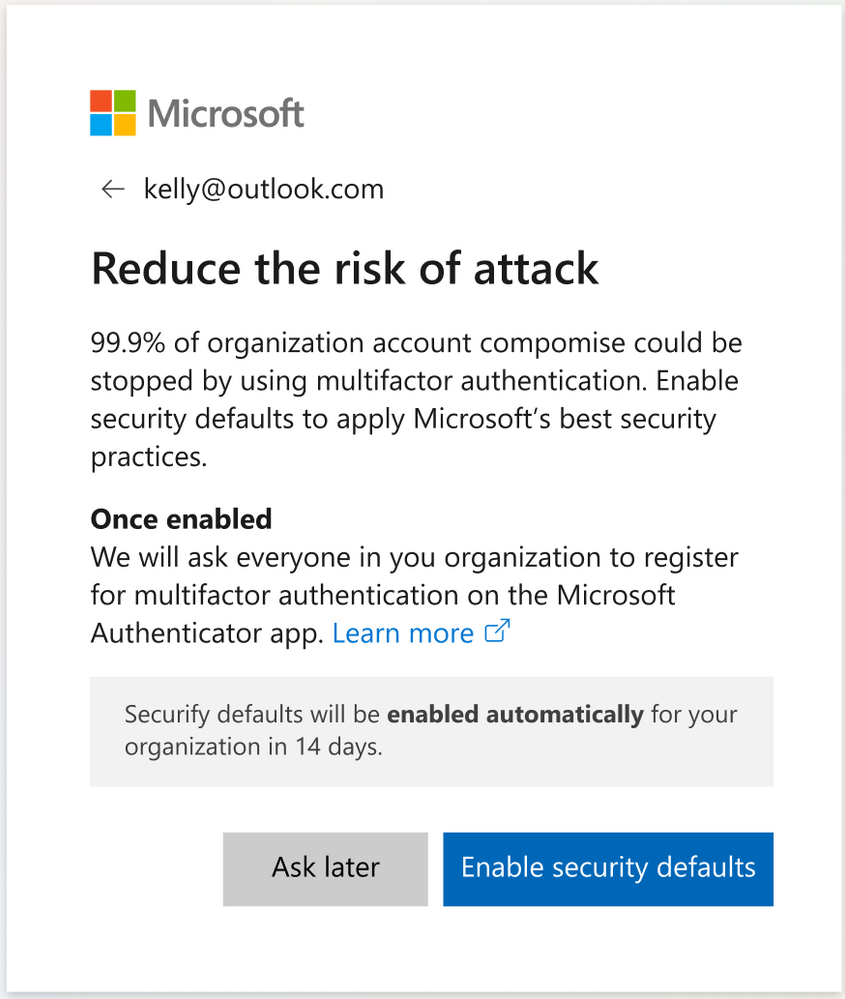
The new security defaults will help protect enterprise user accounts from password spray and phishing attacks by:
- Requiring all users and admins to register for MFA using the Microsoft Authenticator app.
- Challenging users with MFA, mostly when they show up on a new device or app, but more often for critical roles and tasks.
- Disabling authentication from legacy authentication clients that can't do MFA.
- Protecting admins by requiring extra authentication every time they sign in.
Admins who don't want security defaults enabled for their organizations can disable them through the Azure Active Directory properties or the Microsoft 365 admin center.
However, this might be a bad idea since, according to Weinert, organizations who leave security defaults enabled "experience 80 percent less compromise than the overall tenant population."
Furthermore, per Microsoft's telemetry data, requiring MFA prevents over 99.9% of account compromise attacks when enabled.
.jpg)

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now