
A remote code execution flaw in the open-source Apache Commons Text library has some people worried that it could turn into the next Log4Shell. However, most cybersecurity researchers say it is nowhere near as concerning.
Apache Commons Text is a popular open-source Java library with an "interpolation system" that allows developers to modify, decode, generate, and escape strings based on inputted string lookups.
For example, passing the string lookup ${base64Decoder:SGVsbG9Xb3JsZCE=} to the interpolation system would cause the library to convert it to its base64 decoded value of 'HelloWorld!'.
The new CVE-2022-42889 vulnerability in Apache Commons Text, dubbed "Text4Shell," is caused by unsafe script evaluation by the interpolation system that could trigger code execution when processing malicious input in the library's default configuration.
"Starting with version 1.5 and continuing through 1.9, the set of default Lookup instances included interpolators that could result in arbitrary code execution or contact with remote servers," details a developer in the Apache mailing list.
"Applications using the interpolation defaults in the affected versions may be vulnerable to RCE or unintentional contact with remote servers if untrusted configuration values are used."
"Users are recommended to upgrade to Apache Commons Text 1.10.0, which disables the problematic interpolators by default."
The issue was discovered by GitHub's threat analyst Alvaro Munoz and reported to Apache on March 9, 2022.
However, it took the open-source library developers 7 months, until October 12, 2022, to release a fix in version 1.10.0, which disables interpolation.
Should you worry?
Due to the widespread deployment of the vulnerable library, and since the flaw impacts versions that date as far back as 2018, some initially worried that it could cause widespread damage, as we saw with the Log4Shell vulnerability.
However, a report from Rapid7 quickly put a brake to these concerns, explaining that not all versions between 1.5 and 1.9 seem vulnerable and that its exploitation potential was connected to the JDK version used.
Even with an updated proof of concept (PoC) exploit using the JEXL engine as an exploit path bypasses the JDK limitation, researchers are still not very concerned.
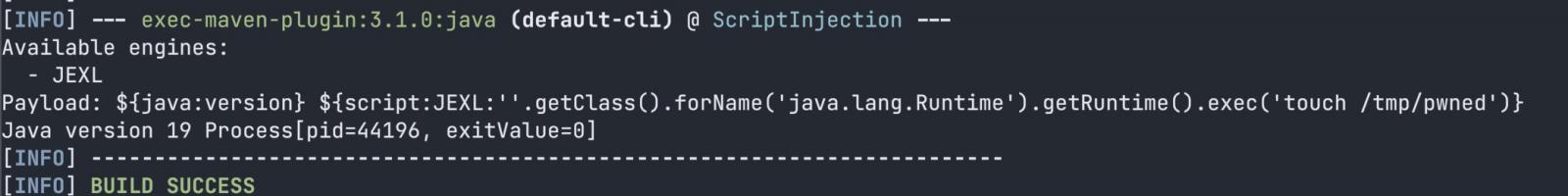
Furthermore, Apache's security team has said that the scope of the flaw is not a serious as Log4Shell, explaining that the string interpolation is a documented feature. Therefore, it’s less likely that applications using the library would inadvertently pass unsafe input without validation.
While the critical severity flaw remained unpatched for seven months and exposed to exploitation attempts, there have been no reports of abuse in the wild even after exploits were released.
While we will likely see some threat actors exploiting CVE-2022-42889 in the future, it will probably be limited in scope.
For now, all developers utilizing the Apache Commons Text library are advised to upgrade to version 1.10 or later as soon as possible to fix the flaw.
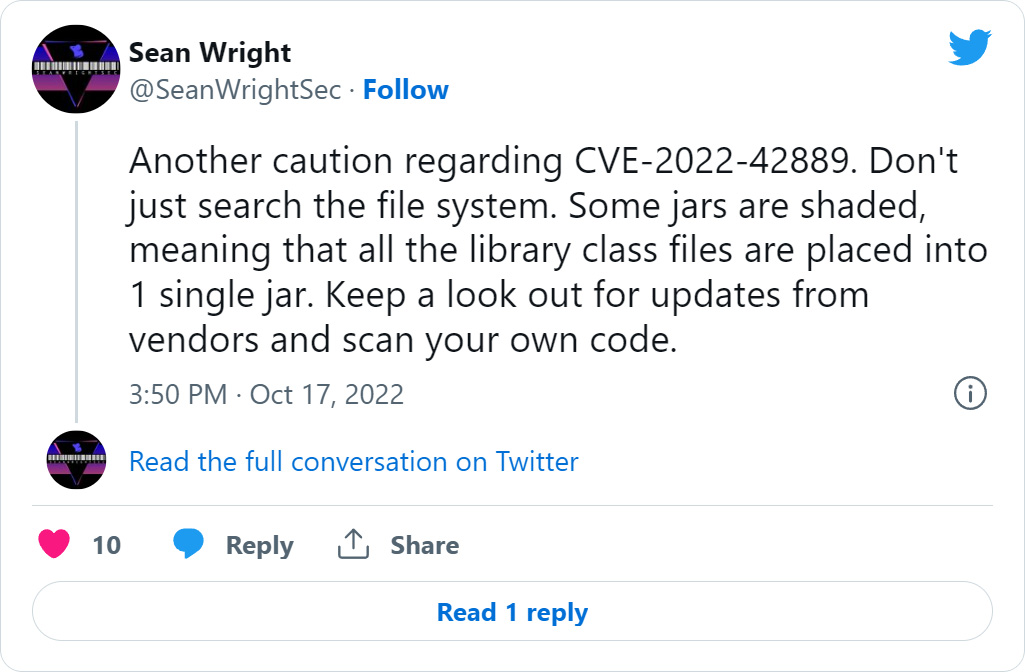
Security researcher Sean Wright warns that some Java projects keep all library class files in a single jar and will need to be scanned independently.
To aid in finding vulnerable versions of the Apache Commons Text library, Silent Signal has released a Burp plugin that can scan apps for components unpatched against CVE-2022-42889.



Comments
h_b_s - 1 year ago
I think it's reasonably arguable that Log4J isn't quite as bad as some of the tech press and some experts were claiming, either. Yes the flaw itself is severe, but the practicalities of actually exploiting it doesn't lead towards mass one-size-fits-all type exploits that other high severity flaws can. Each instance has to be tailor made to the environment being targeted which limits its appeal to those higher up on the attack sophistication tree.
The practicality of exploitation didn't lead towards near immediate mass exploitation via worm attacks as many were claiming.