
Hackers are actively exploiting a high-severity vulnerability in Openfire messaging servers to encrypt servers with ransomware and deploy cryptominers.
Openfire is a widely used Java-based open-source chat (XMPP) server downloaded 9 million times and used extensively for secure, multi-platform chat communications.
The flaw, tracked as CVE-2023-32315, is an authentication bypass impacting Openfire's administration console, allowing unauthenticated attackers to create new admin accounts on vulnerable servers.
Using those accounts, the attackers install malicious Java plugins (JAR files) that execute commands received via GET and POST HTTP requests.
This dangerous flaw impacts all Openfire versions from 3.10.0, dating to 2015, to up to 4.6.7 and from 4.7.0 to 4.7.4.
Although Openfire fixed the issue with versions 4.6.8, 4.7.5, and 4.8.0, released in May 2023, VulnCheck reported that by mid-August 2023, over 3,000 Openfire servers were still running a vulnerable version.
Dr. Web now reports signs of active exploitation, as hackers have taken advantage of the attack surface for their malicious campaigns.
The first case of active exploitation seen by Dr. Web dates to June 2023, when the security firm investigated a server ransomware attack that occurred after CVE-2023-32315 was exploited to breach the server.
The attackers leveraged the flaw to create a new admin user on Openfire, logged in, and used it to install a malicious JAR plugin that can run arbitrary code.
Some of the malicious JAVA plugins seen by Dr. Web and customers include helloworld-openfire-plugin-assembly.jar, product.jar, and bookmarks-openfire-plugin-assembly.jar.
After setting up an Openfire honeypot to capture the malware, Dr. Web caught additional trojans that are used in attacks in the wild.
The first of the additional payloads is a Go-based crypto-mining trojan known as Kinsing.
Its operators exploit CVE-2023-32315 to create an admin account named "OpenfireSupport," and then install a malicious plugin called "plugin.jar" that fetches the miner payload and installs it on the server.
In another case, the attackers installed a C-based UPX-packed backdoor instead, following a similar infection chain.
A third attack scenario observed by Dr. Web's analysts is where a malicious Openfire plugin was used to obtain information about the compromised server, specifically network connections, IP addresses, user data, and the system's kernel version.
Dr. Web has observed a total of four distinct attack scenarios leveraging CVE-2023-32315, making the application of the available security updates exigent.
An unknown ransomware
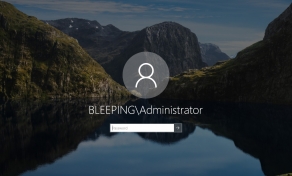
BleepingComputer has found multiple reports from customers saying their Openfire servers were encrypted with ransomware, with one stating that the files were encrypted with the .locked1 extension.
"I am an operator who runs a server using open fire open source in Korea. It's not different, I'm using openfire 4.7.4-1.noarch.rpm, but one day all files in /opt/openfire (openfire installation path) are changed to .locked1 extension," explained an OpenFire admin.
Since 2022, a threat actor has been encrypting exposed web servers with ransomware that appends the .locked1 extension.

Source: BleepingComputer
BleepingComputer is aware of Openfire servers encrypted by this ransomware in June.
It is unclear what ransomware is behind these attacks, but the ransom demands are generally small, ranging from .09 to .12 bitcoins ($2,300 to $3,500).
The threat actor does not appear to solely target Openfire servers, but any vulnerable web server. Therefore, applying all security updates for your servers when they become available is crucial.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now