
Bank of America is warning customers of a data breach exposing their personal information after Infosys McCamish Systems (IMS), one of its service providers, was hacked last year.
Customer personally identifiable information (PII) exposed in the security breach includes the affected individuals' names, addresses, social security numbers, dates of birth, and financial information, including account and credit card numbers, according to details shared with the Attorney General of Texas.
Bank of America serves approximately 69 million clients at over 3,800 retail financial centers and through approximately 15,000 ATMs in the United States, its territories, and more than 35 countries.
A Bank of America spokesperson declined to comment when BleepingComputer reached out for more details and asked us to connect with Infosys McCamish.
While Bank of America has yet to disclose how many customers were impacted by the data breach, an IMS breach notification letter filed with the Attorney General of Maine on behalf of Bank of America revealed that a total of 57,028 people were directly impacted.
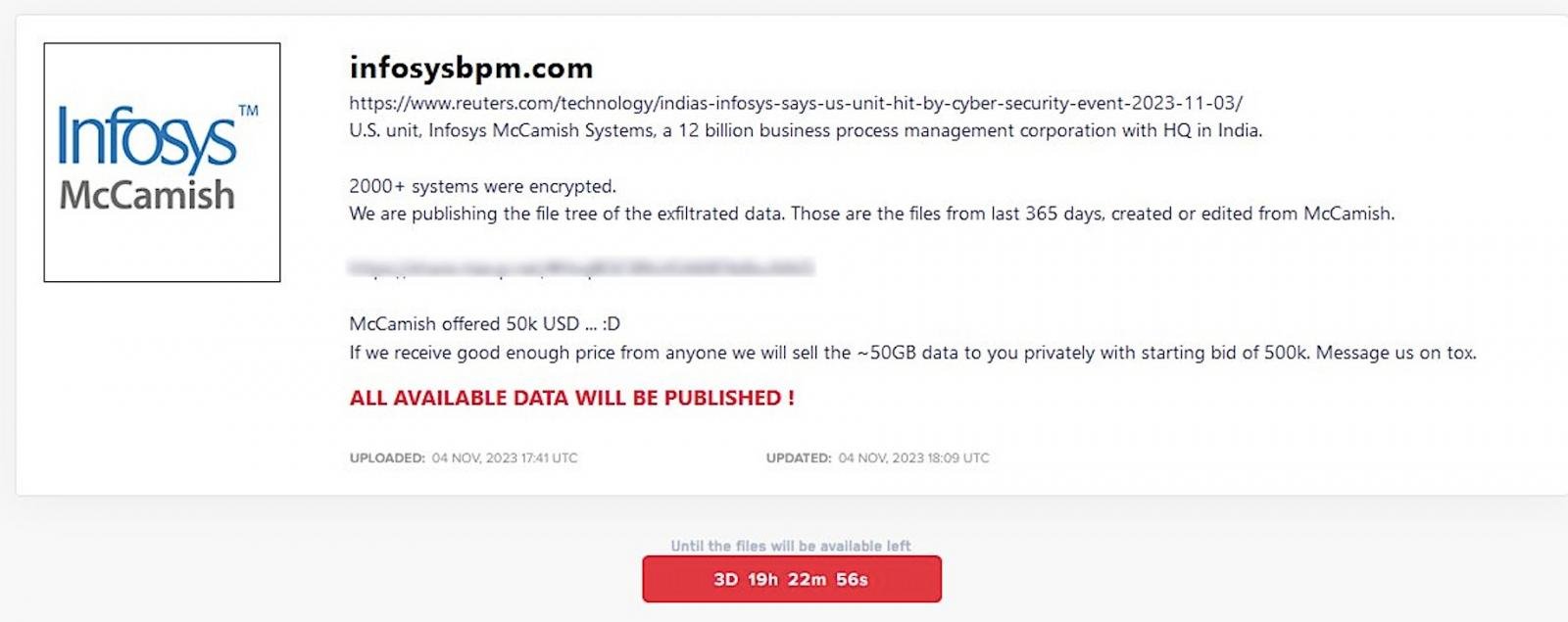
"Or around November 3, 2023, IMS was impacted by a cybersecurity event when an unauthorized third party accessed IMS systems, resulting in the non-availability of certain IMS applications," the data breach notification says.
"On November 24, 2023, IMS told Bank of America that data concerning deferred compensation plans serviced by Bank of America may have been compromised. Bank of America's systems were not compromised."
"It is unlikely that we will be able to determine with certainty what personal information was accessed as a result of this incident at IMS."
LockBit claims ransomware attack on IMS
The November security breach led to a "non-availability of certain applications and systems in IMS," as explained when the incident was first disclosed in a filing with the U.S. Securities and Exchange Commission.
On November 4th, the LockBit ransomware gang claimed responsibility for the IMS attack, saying that its operators encrypted over 2,000 systems during the breach.
The LockBit ransomware-as-a-service (RaaS) operation came to light in September 2019 and has since targeted many high-profile organizations, including the UK Royal Mail, the Continental automotive giant, the City of Oakland, and the Italian Internal Revenue Service.
In June, cybersecurity authorities in the United States and partners worldwide released a joint advisory estimating that the LockBit gang has extorted at least $91 million from U.S. organizations following roughly 1,700 attacks since 2020.
Infosys, IMS' parent company, is a multinational IT consulting and services provider giant with over 300,000 employees and clients in over 56 countries.
An Infosys spokesperson has yet to respond to a BleepingComputer request for confirmation of LockBit's claims and further information about the security breach.
Bank of America customers' financial account information, credit card, social security, and/or other unique government-issued identification numbers handled by leading accounting firm Ernst & Young were also exposed after the service provider's MOVEit Transfer platform got breached in May 2023 by the Clop cybercrime gang.
"Bank of America has informed us that its systems and servers were not impacted by this event," Ernst & Young disclosed in a filing with the Maine Attorney General, revealing that the May 2023 incident affected 30,210 individuals.
Update February 13, 03:24 EST: Bank of America declined to comment.


Comments
BBDogs - 2 months ago
I've had BOA for so long and it has been great but now that my income has dropped I am feeling the fees plus there are hardly any branches open. I'd go with Self or any other bank that doesn't charge fees. Be sure to read the small print. It's difficult to change banks when you have set up payments and deposits plus it could effect your credit rate. I honestly think BOA is going after those with higher balances and is confirming to online banking but it's fees haven't changed. Capital One is now much better than BOA. BOA is pricing itself out of many market segments and derogatory articles aren't helping it's stock price or long fought reputation. Welcome to 2024
Kimjessica - 2 months ago
So I also been with BOA and felt totally unappreciated for my 15yrs with them. I had someone trick me into believing they were a collection agency aha asked they send the contract in the mail after I get it and call them to say it's OK move forward they can start taking $50 a month. Well almost 2 months later I never got a contract or anything from them but they made themselves out a check for $100 so I reported it asked to shut down that account and obviously anything that I had paid prior to this check being made is me, so I thought that made sense. Well they actually returned a auto pay to my credit card with them made 2 weeks prior then get this canceled my credit card for that reason( which was ridiculous if you ask me!!) They knew that was autopay to them every month and then her the other reason; because I used my credit card too much!!! I did it because all my auto pay bills weren't being paid while I waited for them to set up a new checking account and then had to call to get my money released from the hacked account to the new one. I paid the full amount down that u charged, all but $100!!!! They ruined my credit with their claims of over use and returned payment and get this they turned the card back on without sending any apology or anything!!!!! I'm looking for a new bank ATM I was not aware this was one of the 2 banks foreclosing on families during that depression/recession we had. Wells Fargo was the other evil bank. They were who I left to go to BOA. Crazy how after showing I can manage my money for 15yrs they attack me because I was attacked!!