
The North Korean APT hacking group Kimsuky is exploiting ScreenConnect flaws, particularly CVE-2024-1708 and CVE-2024-1709, to infect targets with a new malware variant dubbed ToddlerShark.
Kimsuky (aka Thallium and Velvet Chollima) is a North Korean state-sponsored hacking group known for cyber espionage attacks on organizations and governments worldwide.
The threat actors are exploiting authentication bypass and remote code execution flaws disclosed on February 20, 2024, when ConnectWise urged ScreenConnect customers to immediately upgrade their servers to version 23.9.8 or later.
Public exploits for the two flaws were released the next day, and hackers, including ransomware actors, quickly began leveraging them in actual attacks.
According to a report Kroll's cyber-intelligence team shared with BleepingComputer, the new Kimsuky malware, which exhibits polymorphic traits, appears to have been designed for long-term espionage and intelligence gathering.
ToddlerShark uses legitimate Microsoft binaries to minimize its trace, performs registry modifications to lower security defenses, and establishes persistent access through scheduled tasks, followed by a phase of continual data theft and exfiltration.
ToddlerShark details
Kroll's analysts estimate that ToddlerShark is a new variant of Kimsuky's BabyShark and ReconShark backdoors, previously seen targeting government organizations, research centers, universities, and think tanks in the United States, Europe, and Asia.
The hackers first gain initial access to vulnerable ScreenConnect endpoints by exploiting the vulnerabilities, which give them authentication bypass and code execution capabilities.
Having established a foothold, Kimsuky uses legitimate Microsoft binaries, such as mshta.exe, to execute malicious scripts like a heavily obfuscated VBS, blending its activities with normal system processes.
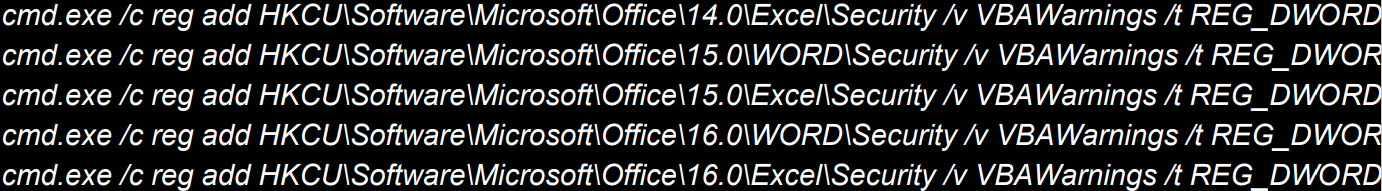
Next, the malware changes VBAWarnings keys in Windows Registry to allow macros to run on various Microsoft Word and Excel versions without generating notifications.
Scheduled tasks are created to establish persistence by periodically (every minute) executing the malicious code.
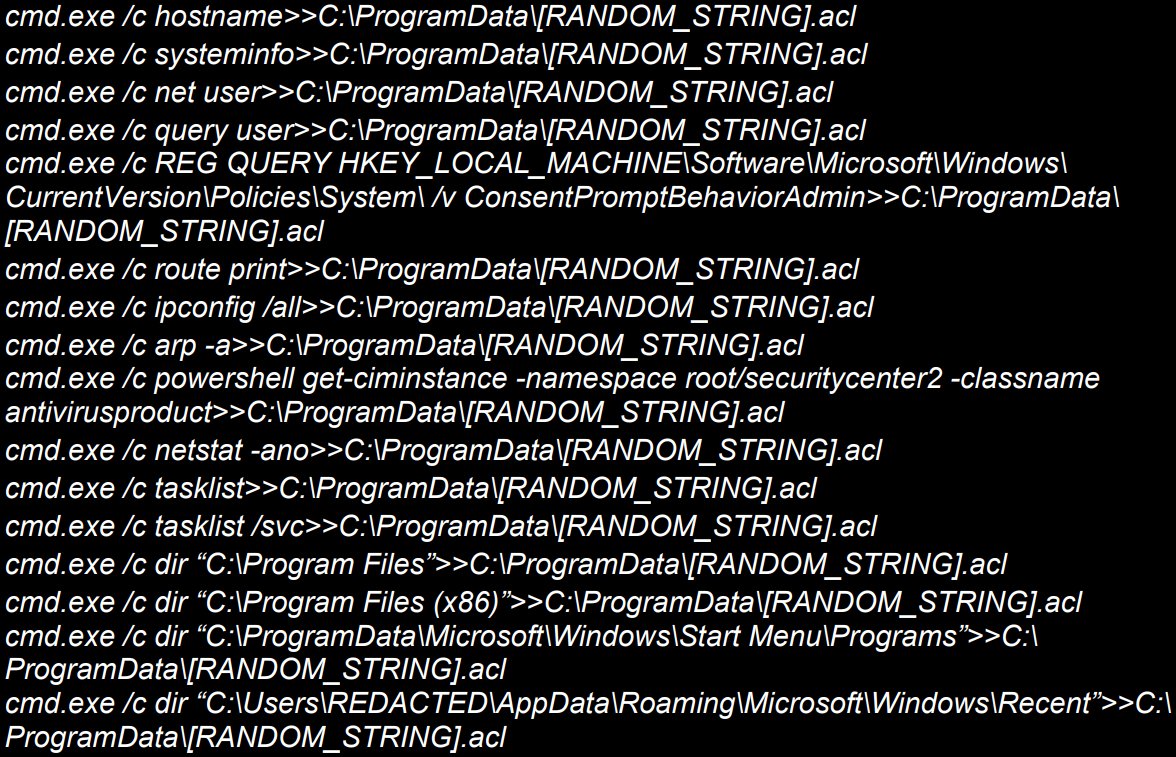
ToddlerShark routinely gathers system information from infected devices, including the following:
- Hostname
- System configuration details
- User accounts
- Active user sessions
- Network configurations
- Security software installed
- All current network connections
- Enumeration of running processes
- List installed software by parsing common installation paths and Windows Start Menu
Finally, ToddlerShark encodes the gathered information in Privacy Enhanced Mail (PEM) certificates, exfiltrated to the attacker's command and control (C2) infrastructure, an advanced and known Kimsuky tactic.
Polymorphic malware
A notable ability of the new malware is polymorphism, which allows it to evade detection in many cases and make analysis more challenging. ToddlerShark achieves this through several techniques.
First, it uses randomly generated functions and variable names in the heavily obfuscated VBScript used in the initial infection step, making static detection harder. Large amounts of hexadecimal encoded code interspersed with junk code may make the malware payload appear benign or non-executable.
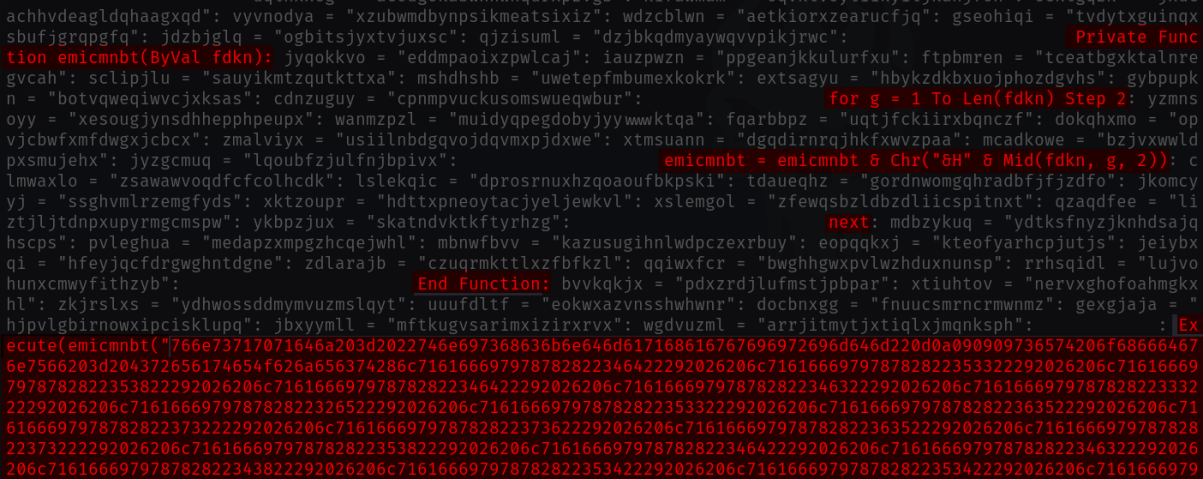
Additionally, ToddlerShark employs randomized strings and [functional] code positioning, which alters its structural pattern enough to make signature-based detection ineffective against it.
Finally, the URLs used for downloading additional stages are dynamically generated, and the hash of the initial payload fetched from the C2 is always unique, so standard blocklisting methods are rendered powerless.
Specific details and (indicators of compromise) IoCs relating to ToddlerShark will be shared by Kroll via a blog post on its website tomorrow.
Update 3/5 - Malware name corrected to ToddlerShark


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now