
A financially motivated hacking group named Magnet Goblin uses various 1-day vulnerabilities to breach public-facing servers and deploy custom malware on Windows and Linux systems.
1-day flaws refer to publicly disclosed vulnerabilities for which a patch has been released. Threat actors looking to exploit these flaws must do so quickly before a target can apply security updates.
Though exploits are usually not made available immediately upon a flaw's disclosure, some vulnerabilities are trivial to figure out how to leverage. Additionally, reverse-engineering the patch may reveal the underlying problem and how to exploit it.
Check Point analysts who identified Magnet Goblin report that these threat actors are quick to exploit newly disclosed vulnerabilities, in some cases exploiting flaws a day after a PoC exploit is released.
Some of the devices or services targeted by the hackers are Ivanti Connect Secure (CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, CVE-2024-21893., Apache ActiveMQ, ConnectWise ScreenConnect, Qlik Sense (CVE-2023-41265, CVE-2023-41266, CVE-2023-48365), and Magento (CVE-2022-24086).
Magnet Goblin exploits the flaws to infect servers with custom malware, particularly NerbianRAT and MiniNerbian, as well as a custom variant of the WARPWIRE JavaScript stealer.
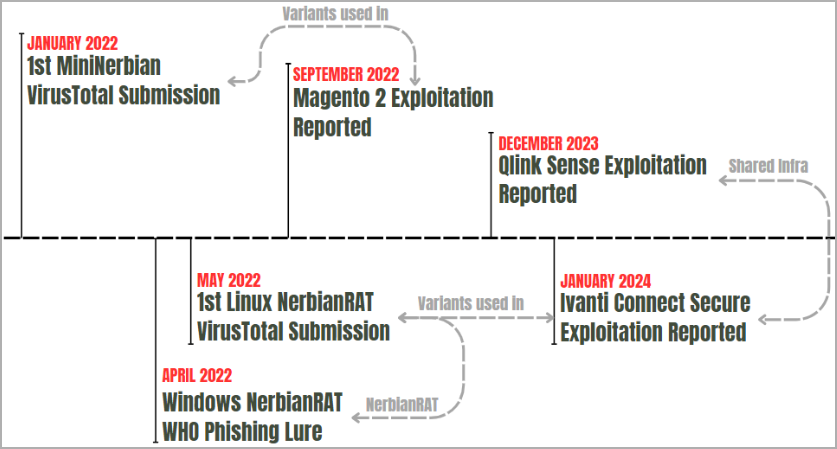
Source: Check Point
Custom Linux malware
NerbianRAT for Windows has been known since 2022, but Check Point now reports that a sloppily compiled yet effective Linux variant used by Magnet Goblin has been in circulation since May 2022.
Upon first launch, the malware performs preliminary actions, including the collection of system info such as time, username, and machine name, generation of a bot ID, setting a hardcoded IP address as primary and secondary host, setting the working directory, and loading a public RSA key for encrypting (AES) network communication.
After that, NerbianRAT loads its configuration, which determines activity times (worktime), time intervals for communicating with the command and control (C2) server, and other parameters.
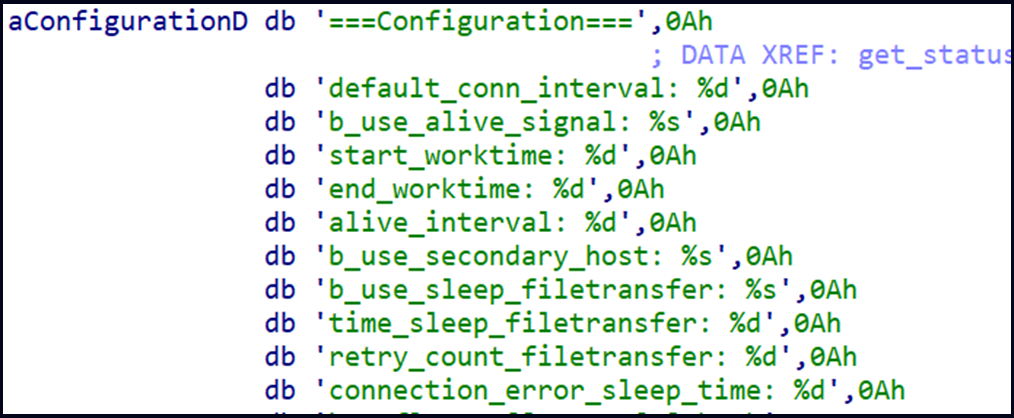
Source: Check Point
The C2 may send one of the following actions to the malware for execution at the infected system:
- Request more actions
- Execute a Linux command in a new thread
- Send command result and clean the file; stop any running commands
- Execute a Linux command immediately
- Do nothing
- Modify connection interval
- Adjust and save worktime settings
- Return idle timings, config, or command results
- Update a specific config variable
- Refresh command buffer for C2 execution commands
The MiniNerbian is a simplified version of the NerbianRAT, which is primarily used for command execution and supports the following actions:
- Execute C2's command and return results
- Update activity schedule (full day or specific hours)
- Update configuration
MiniNerbian communicates with the C2 via HTTP, differentiating it from the more complex NerbianRAT, which uses raw TCP sockets for communication.
Possibly, Magnet Goblin uses it for redundancy or as a stealthier backdoor in some cases.
Source: Check Point
Check Point says identifying specific threats like Magnet Goblin's attacks among the sheer volume of 1-day exploitation data is challenging, allowing these groups to hide in plain sight in the chaos that follows the disclosure of flaws.
Patching quickly is critical in beating 1-day exploitation, while additional measures such as network segmentation, endpoint protection, and multi-factor authentication can help mitigate the impact of potential breaches.


Comments
wpontius - 1 month ago
If the lack of patching for WannaCry is any indication, they have years of exploitation left.