
Fast Shop, one of Brazil's largest retailers, has suffered an 'extortion' cyberattack that led to network disruption and the temporary closure of its online store.
Fast Shop is an online retailer selling a wide range of products, including computers, smartphones, gaming consoles, furniture, beauty products, and home appliances. The retailer has been active in Brazil since 1986 and currently operates 86 physical locations, with its website and app counting over six million visits monthly.
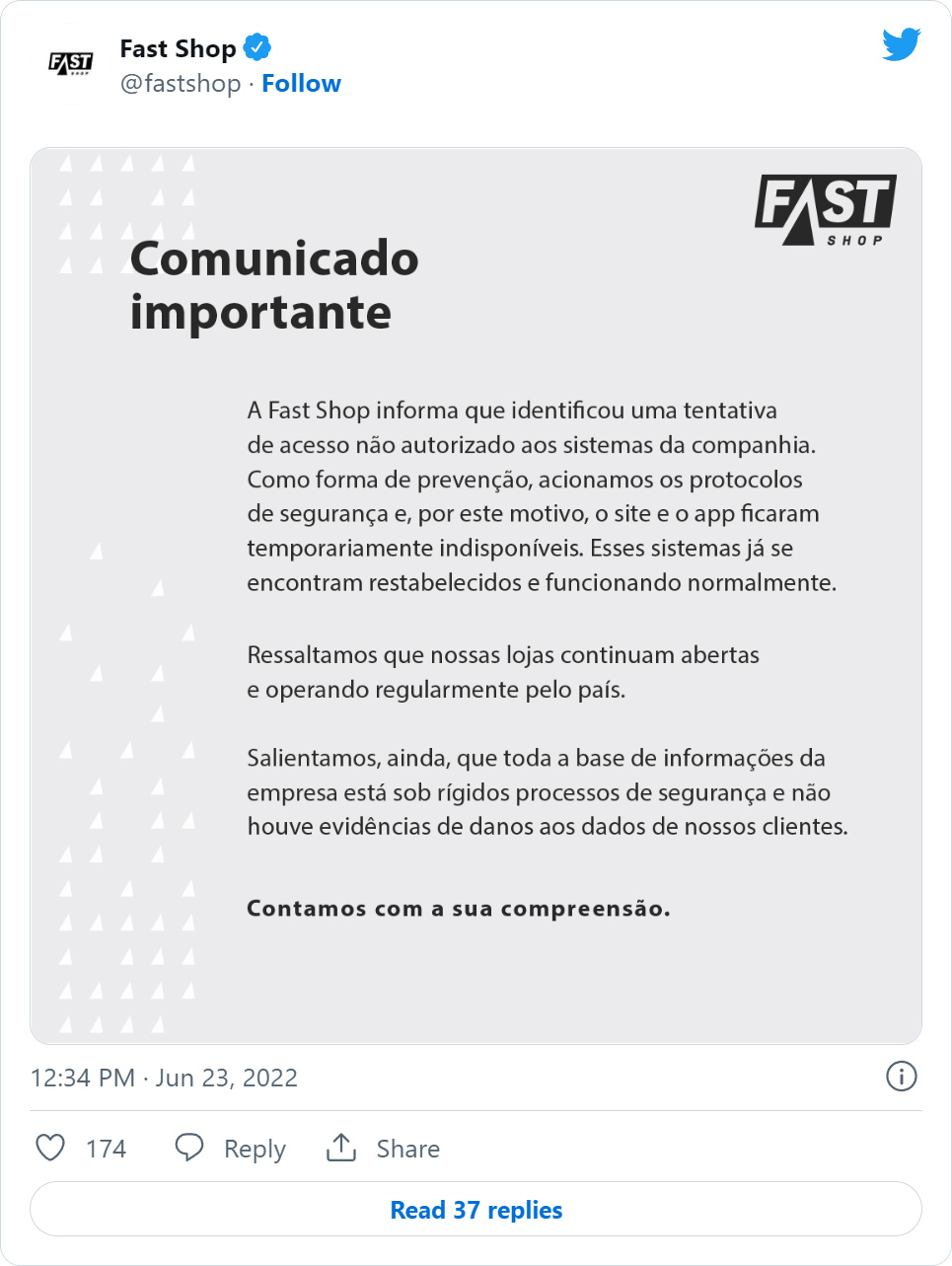
The cyberattack occurred Wednesday, impacting the Fast Shop main website, mobile apps, and online ordering system, as the retailer took systems offline as part of its incident response protocol. The attack didn't impact physical shops.
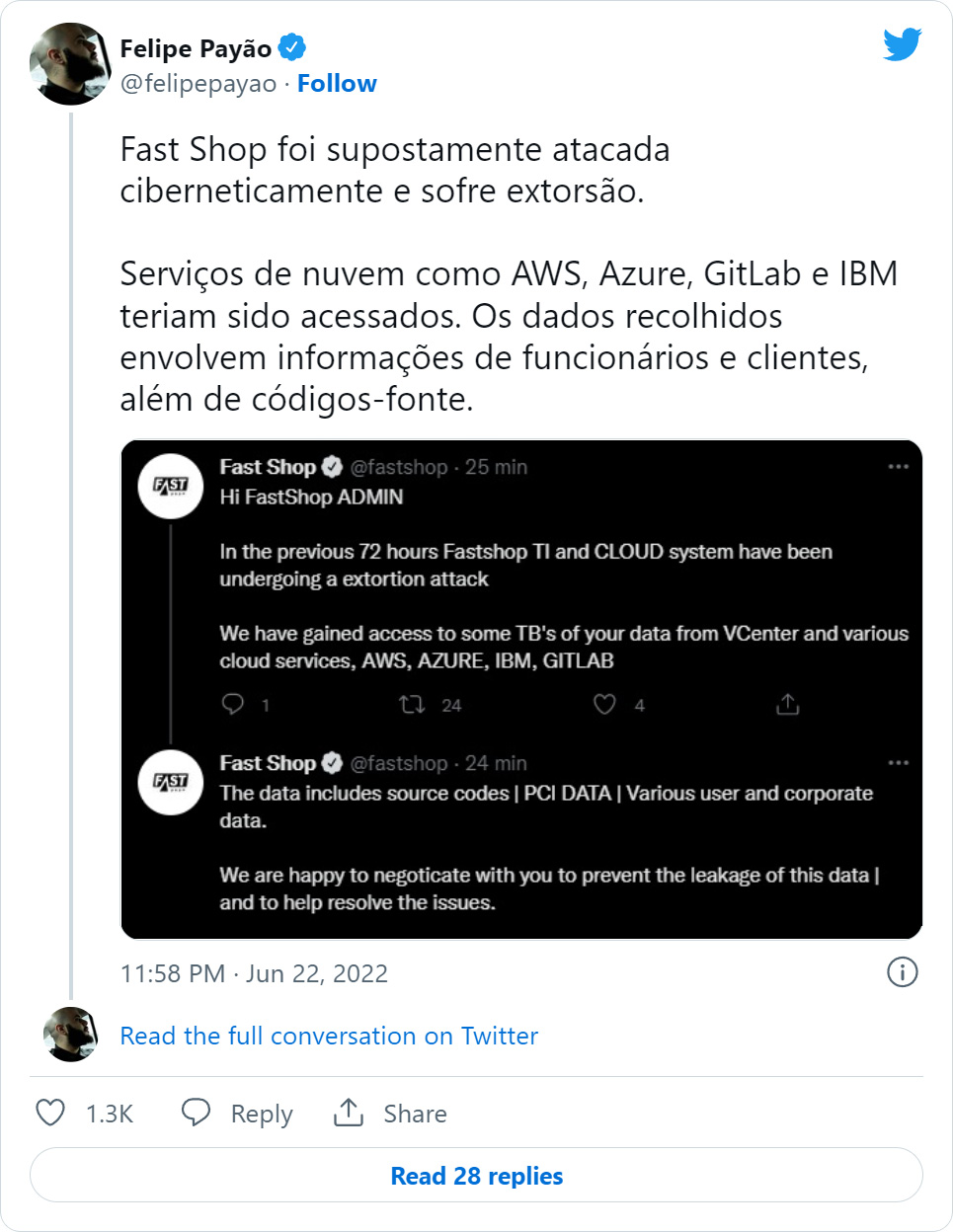
Followers of Fast Shop's Twitter handle learned about the situation a little earlier, as the network intruders took over the firm's Twitter account to announce that they had performed a data breach.
The threat actors claimed that over the past 72 hours, they were actively extorting Fast Shop after accessing the firm's databases on AWS, Azure, GitLab, and IBM cloud, stealing website/app source code and valuable user and corporate data.
Threat actors allegedly used the stolen information to blackmail Fast Shop into paying a ransom; otherwise, all data would be leaked to the public.
Notably, Fast Shop is soon to launch a new online platform focusing on augmented reality and artificial intelligence, so the stolen source code might include valuable project details.
The threat actor's messages were removed when Fast Shop's admins regained control of the compromised Twitter account. However, Tec Mundo's infosec news reporter, Felipe Payao, was able to save a screenshot.
Fast Shop's announcement has responded to these claims, saying that they see no evidence of customer data having been compromised, and the same applies to the firm's "entire information base."
While Fast Shop is disputing the hacker's claims, everyone who has an account on the Brazilian e-commerce platform should reset their passwords if they use the same credentials on other websites.
From the available information, this looks like a data extortion attack rather than a traditional ransomware attack. Similar to those launched by the now-defunct Lapsus group, which extorted victims with the main threat to publish stolen data.
Bleeping Computer has requested more information about the cyberattack from Fast Shop, and we will update this post when we receive a response.

.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now