Implementing Password Security
SiteLock
AUGUST 27, 2021
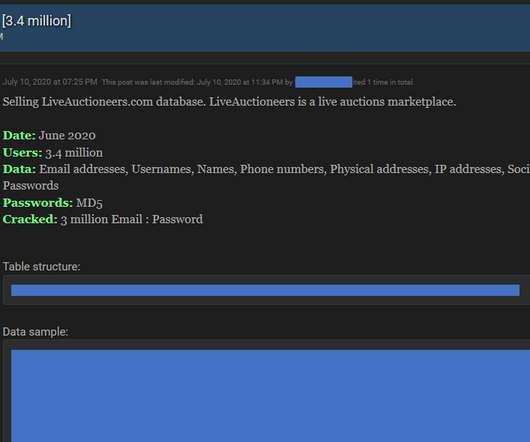
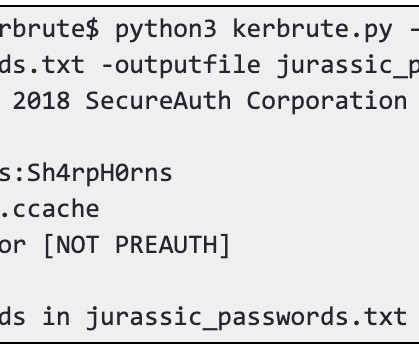
Seems like every few months another blogger or security maven laments the passing of the password, a security tool that has outlived its usefulness and should now be replaced with something more of the times, more effective, more secure. And while the password might be on life-support, it’s not quite gone. That’s right.






















Let's personalize your content