New TunnelVision technique can bypass the VPN encapsulation
Security Affairs
MAY 8, 2024
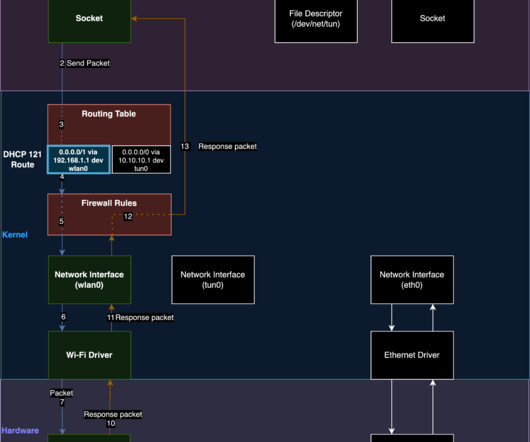
The technique causes the VPN to fail to encrypt certain packets, leaving the traffic vulnerable to snooping. The researchers speculate that the vulnerability existed in DHCP since 2002, when option 121 was implemented. The researchers referred to this result as “decloaking.”














Let's personalize your content