Ransomware Gangs and the Name Game Distraction
Krebs on Security
AUGUST 5, 2021
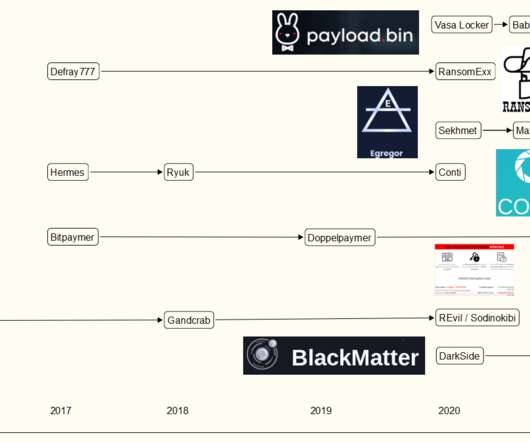
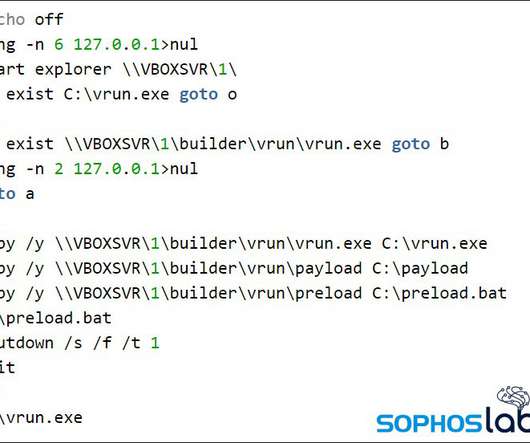
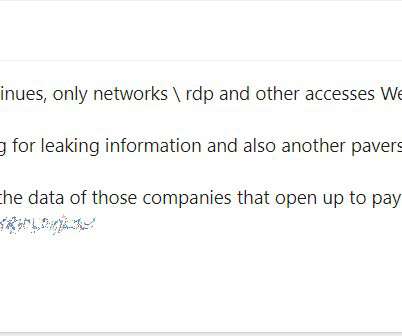
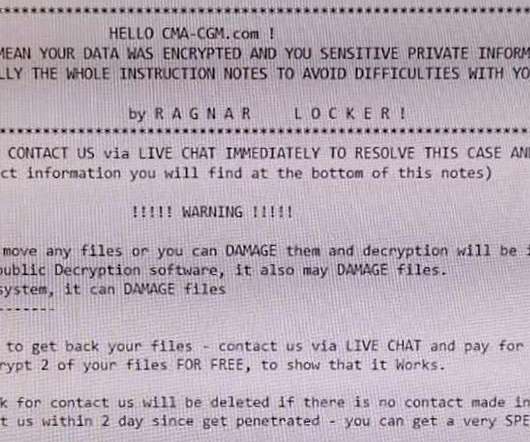
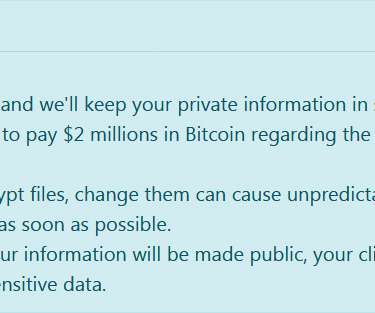
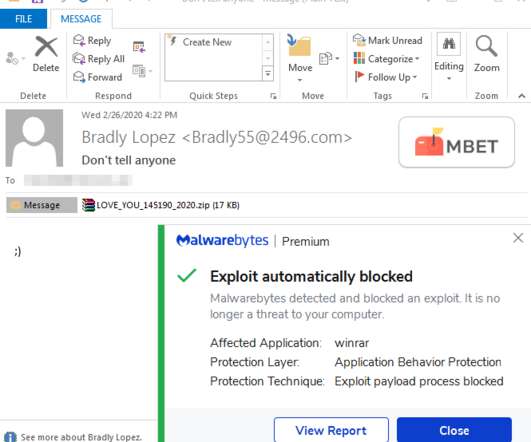
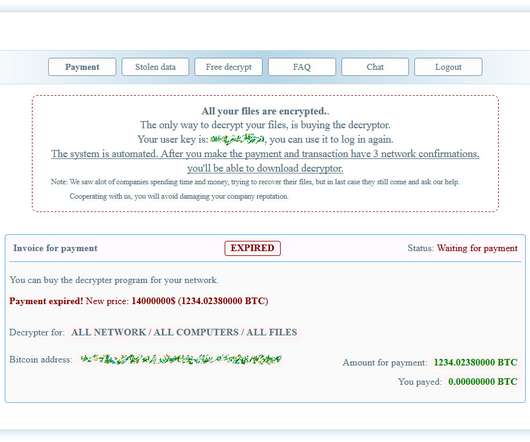
It’s nice when ransomware gangs have their bitcoin stolen, malware servers shut down, or are otherwise forced to disband. Indeed, some of the most destructive and costly ransomware groups are now in their third incarnation. Indeed, some of the most destructive and costly ransomware groups are now in their third incarnation.





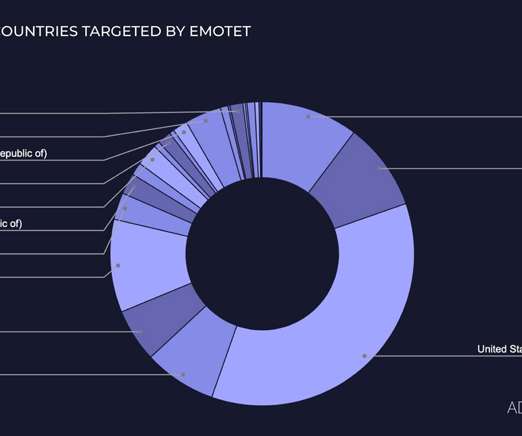
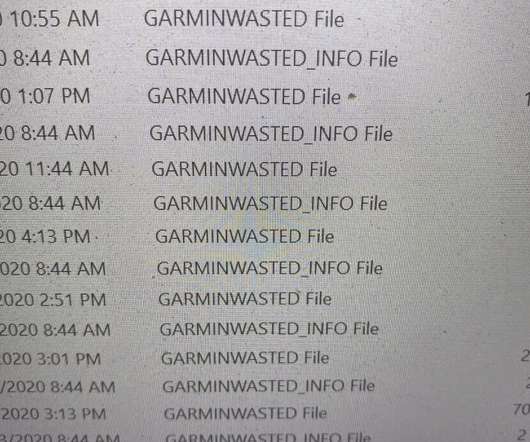

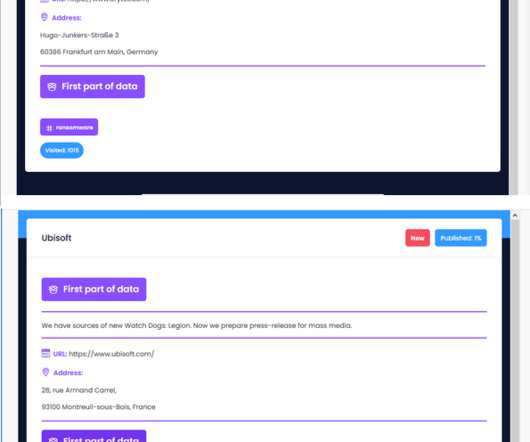
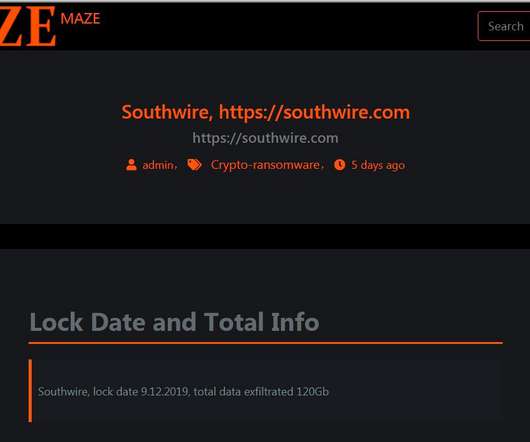
























Let's personalize your content