2021 Data Threat Report: How Covid Changed Everything
Thales Cloud Protection & Licensing
JUNE 2, 2021
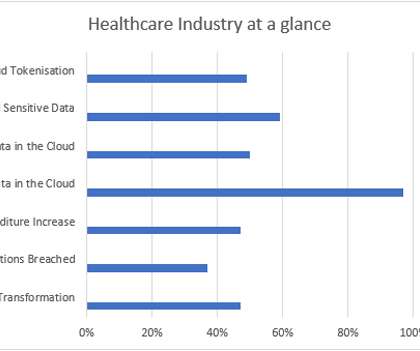
2021 Data Threat Report: How Covid Changed Everything. The 2021 Thales Data Threat Report serves exactly this purpose – it is a crucial reflection of 2020. Only 17% indicated that they have protected more than 50% of their sensitive cloud data with encryption. Cloud Encryption Gateway. Data security.















Let's personalize your content