Threat actors are actively exploiting Zerologon flaw, Microsoft warns
Security Affairs
OCTOBER 30, 2020
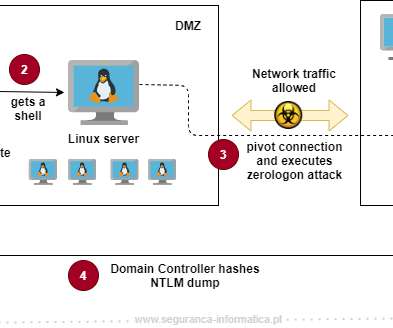
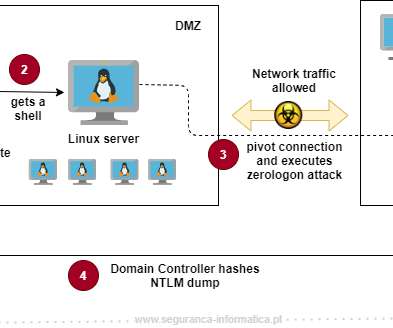
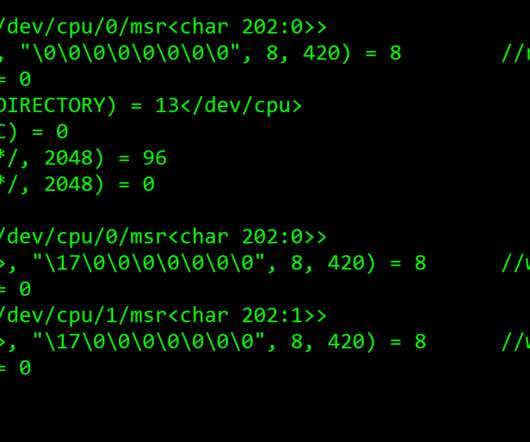
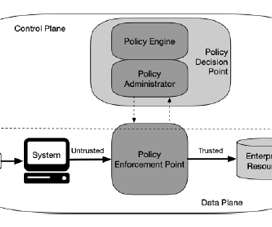
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.

























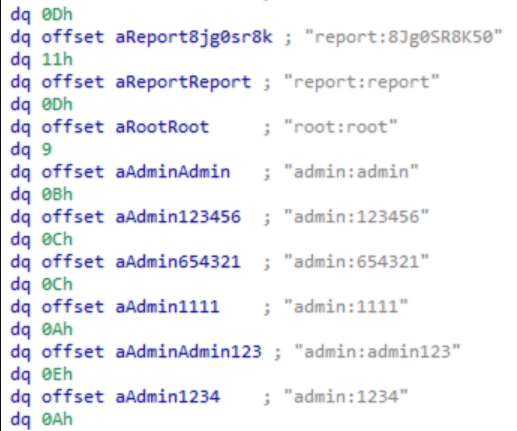

















Let's personalize your content