Lessons from a Scam Artist
Security Through Education
MARCH 22, 2023
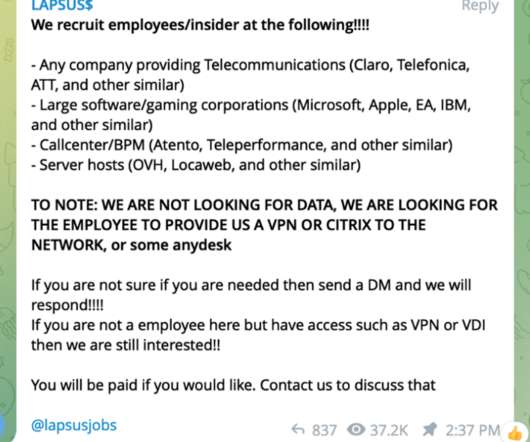
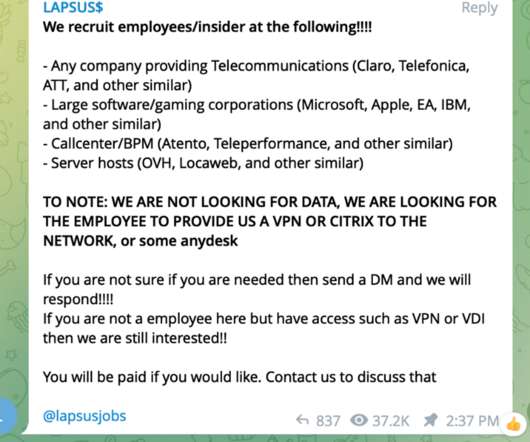
They all use psychology and social engineering skills to convince their victims to take an action that is detrimental to them. Impersonators create fake social media accounts that include the names, images, logos, or other identifying information, of a person, brand, or organization. billion fake accounts in 2021.















































Let's personalize your content