Elevate Your IAM Strategy with Thales at EIC 2024
Thales Cloud Protection & Licensing
MAY 29, 2024
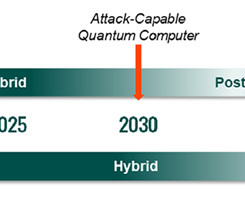
Elevate Your IAM Strategy with Thales at EIC 2024 madhav Thu, 05/30/2024 - 05:23 From 4 to 7 June, Berlin will host Europe’s premier identity and cloud experts gathering. One not-to-be-missed session is our keynote, “ Can you trust AI in IAM?
















































Let's personalize your content