The mobile malware threat landscape in 2022
SecureList
FEBRUARY 27, 2023
Figures of the year In 2022, Kaspersky mobile products and technology detected: 1,661,743 malicious installers 196,476 new mobile banking Trojans 10,543 new mobile ransomware Trojans Trends of the year Mobile attacks leveled off after decreasing in the second half of 2021 and remained around the same level throughout 2022. percentage points.


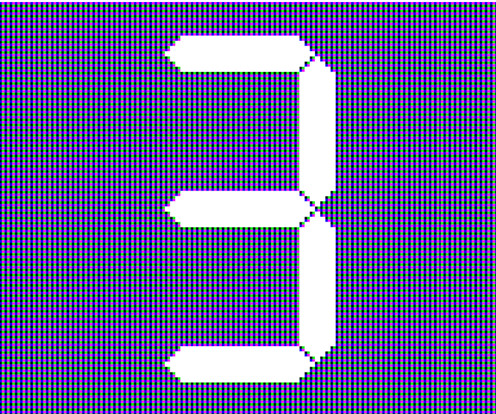
























Let's personalize your content