Duo vs. Fraudulent Device Registration
Duo's Security Blog
APRIL 8, 2024
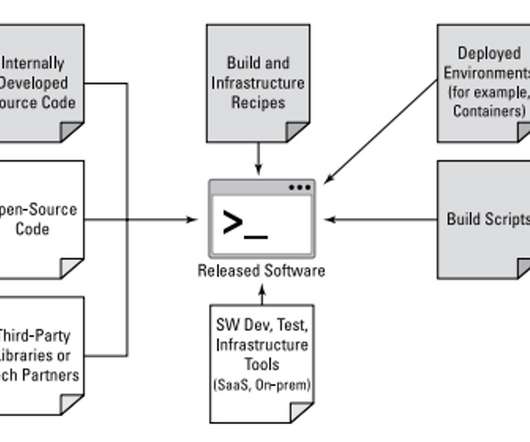
It is a well-known and established point that a password alone is not enough to secure an account. That’s where multi-factor authentication (MFA) comes in. But what if an attacker can just send that authentication request to their own personal phone? This type of attack is known as Account Manipulation: Device Registration.





























Let's personalize your content