Check Point released hotfix for actively exploited VPN zero-day
Security Affairs
MAY 29, 2024
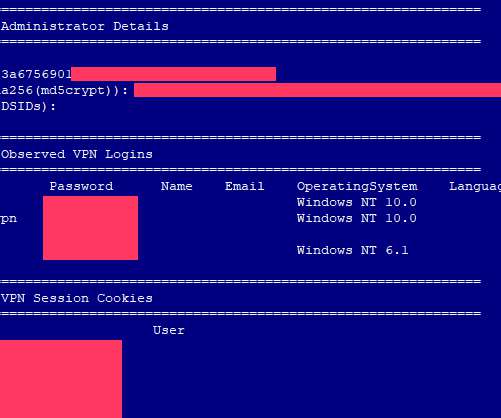
Check Point released hotfixes for a VPN zero-day vulnerability, tracked as CVE-2024-24919, which is actively exploited in attacks in the wild. Check Point released hotfixes to address a VPN zero-day vulnerability, tracked as CVE-2024-24919 , which is actively being exploited in attacks in the wild.















































Let's personalize your content