T-Mobile confirms Lapsus$ had access its systems
Security Affairs
APRIL 23, 2022
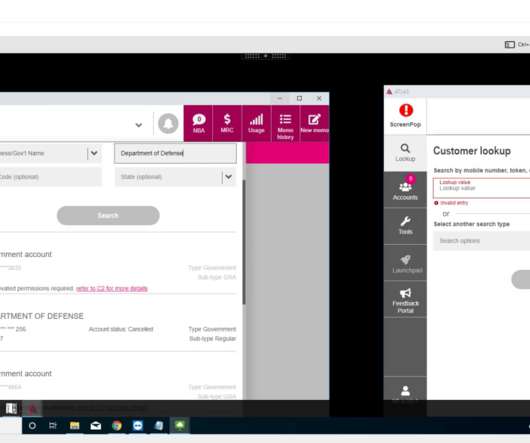
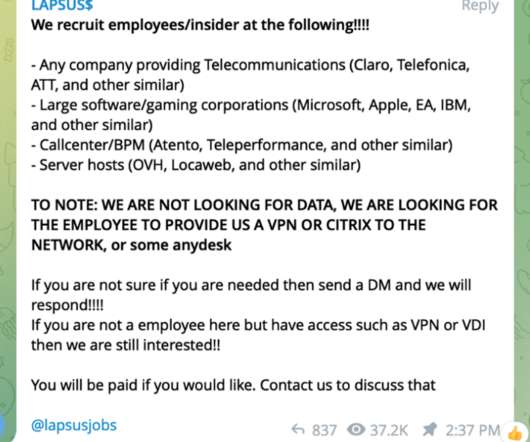
Telecommunication giant T-Mobile confirmed the LAPSUS$ extortion group gained access to its networks in March. Telecom company T-Mobile on Friday revealed that LAPSUS$ extortion gang gained access to its networks. ” LAPSUS$ leader White/Lapsus Jobs looking up the Department of Defense in T-Mobile’s internal Atlas system.













































Let's personalize your content