Iran-linked MERCURY APT behind destructive attacks on hybrid environments
Security Affairs
APRIL 10, 2023
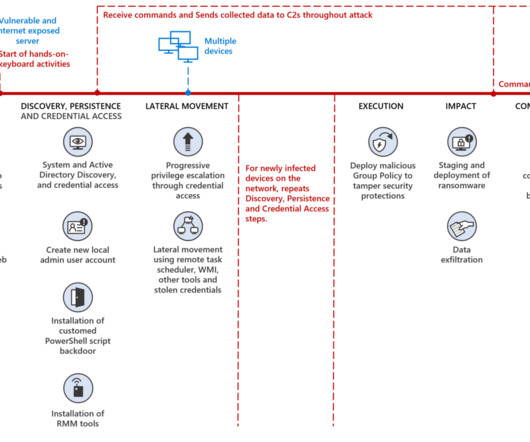
. “DEV-1084 was then later observed leveraging highly privileged compromised credentials to perform en masse destruction of resources, including server farms, virtual machines, storage accounts, and virtual networks, and send emails to internal and external recipients.” Both groups used MULLVAD VPN.












Let's personalize your content