Latin American Javali trojan weaponizing Avira antivirus legitimate injector to implant malware
Security Affairs
FEBRUARY 16, 2021
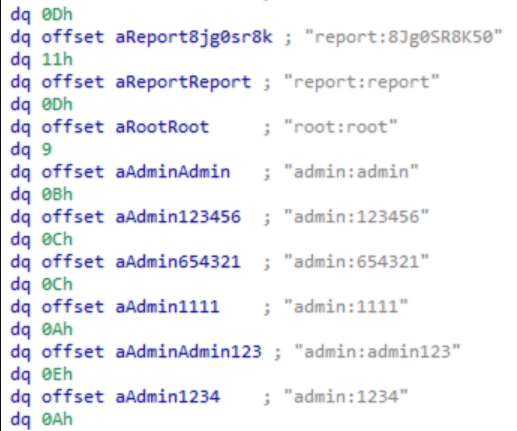
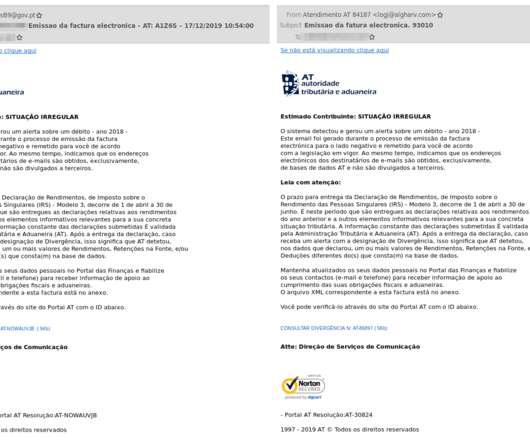
Latin American Javali trojan weaponizing Avira antivirus legitimate injector to implant malware. As mentioned, in general, this trojan was developed using the same architecture of other Latin American trojans, and the main steps of the infection chain are described below and analyzed in-depth during the next sections of this article.














Let's personalize your content