Detecting DNS implants: Old kitten, new tricks – A Saitama Case Study
Fox IT
AUGUST 11, 2022
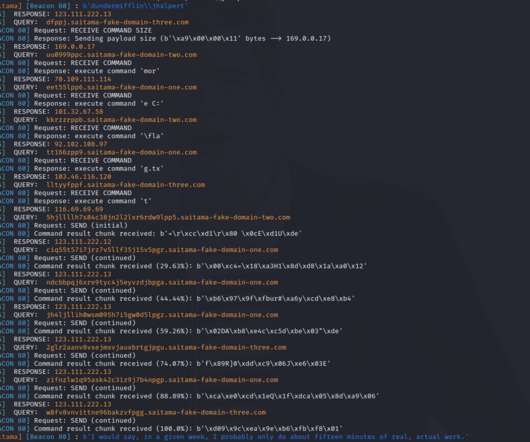
This Saitama implant uses DNS as its sole Command and Control channel and utilizes long sleep times and (sub)domain randomization to evade detection. In May 2022, security firm Malwarebytes published a two 1 -part 2 blog about a malware sample that utilizes DNS as its sole channel for C2 communication. Introduction.



















Let's personalize your content