Symbiote, a nearly-impossible-to-detect Linux malware?
Security Affairs
JUNE 9, 2022
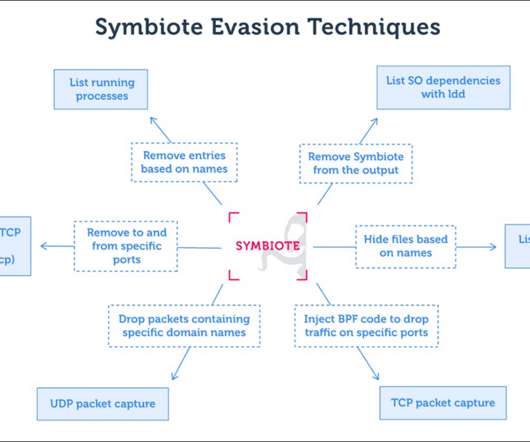
“Network telemetry can be used to detect anomalous DNS requests, and security tools such as antivirus and endpoint detection and response (EDR) should be statically linked to ensure they are not “infected” by userland rootkits.” ” concludes the report. Follow me on Twitter: @securityaffairs and Facebook.












Let's personalize your content