Symbiote, a nearly-impossible-to-detect Linux malware?
Security Affairs
JUNE 9, 2022
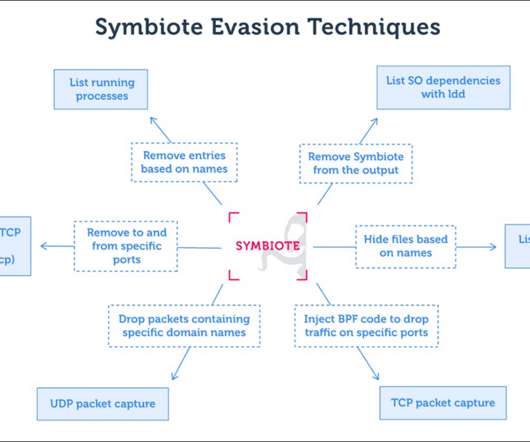
Researchers uncovered a high stealth Linux malware, dubbed Symbiote, that could be used to backdoor infected systems. Joint research conducted by security firms Intezer and BlackBerry uncovered a new Linux threat dubbed Symbiote. “Symbiote is a malware that is highly evasive. ” concludes the report.































Let's personalize your content