Emerging Trends in Cybersecurity: Strategies to Combat Cyber Extortion Attacks on Businesses in 2023
Cytelligence
OCTOBER 5, 2023
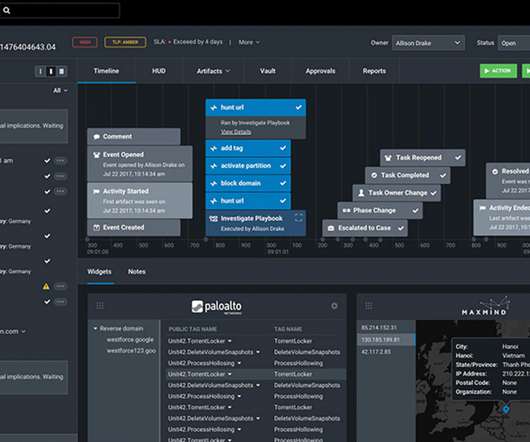
As we passed the halfway point of 2023, businesses must stay ahead of emerging trends in cybersecurity and adopt effective strategies to combat these threats. Below, we explore the evolving landscape of cyber extortion attacks and highlight the role of CYPFER, a leading cybersecurity company, in helping businesses protect themselves.
























Let's personalize your content