Adventures in Contacting the Russian FSB
Krebs on Security
JUNE 7, 2021
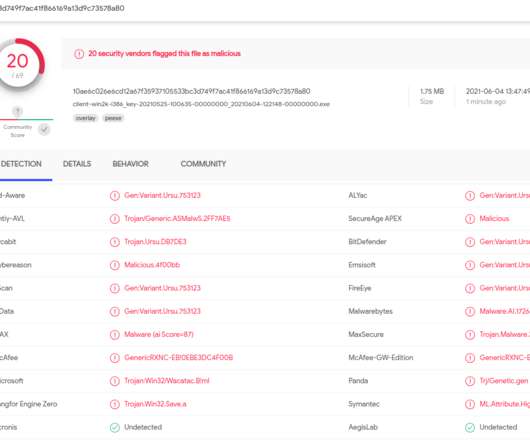
In the process of doing so, I encountered a small snag: The FSB’s website said in order to communicate with them securely, I needed to download and install an encryption and virtual private networking (VPN) appliance that is flagged by at least 20 antivirus products as malware. Image: Wikipedia. biz, circa 2007.








































Let's personalize your content