Microsoft Defender uses Intel TDT technology against crypto-mining malware
Security Affairs
APRIL 27, 2021
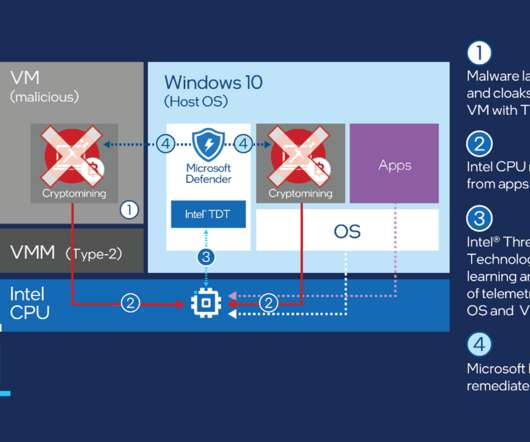
Microsoft announced an improvement of its Defender antivirus that will leverage Intel’s Threat Detection Technology (TDT) to detect processes associated with crypto-miners. ” reads the announcement published by Microsoft.


















































Let's personalize your content