Experts spotted Syslogk, a Linux rootkit under development
Security Affairs
JUNE 14, 2022
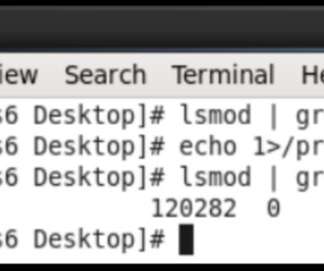
The experts pointed out that it also allows authenticated user-mode processes to interact with the rootkit to control it. Linux rootkits are malware installed as kernel modules in the operating system. Experts highlighted that the kernel rootkit is hard to detect, it enables hiding processes, files, and even the kernel module.












Let's personalize your content