Rapidly executing on SASE vision with new cloud security enhancements
Cisco Security
MAY 17, 2021
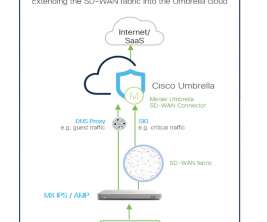
Which architecture should you choose for worldwide delivery of performant connectivity and top-notch security? This is what SASE (Secure Access Service Edge) is all about, and here at Cisco, we’ve spent the last few years perfecting the architecture and approach to help our customers address their new and evolving needs.























Let's personalize your content