Next-Generation Firewalls: A comprehensive guide for network security modernization
CyberSecurity Insiders
JUNE 20, 2023
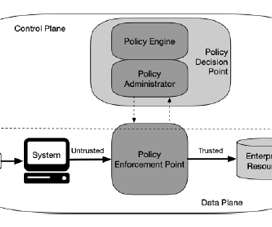
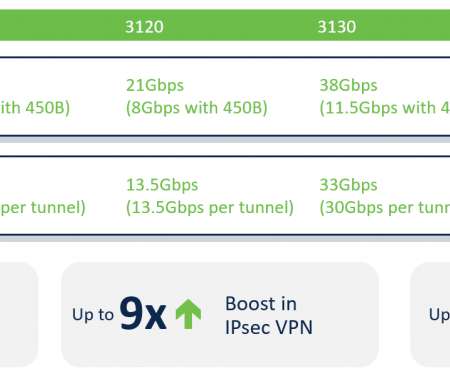
NGFWs boast critical security features such as intrusion prevention, VPN, anti-virus, and encrypted web traffic inspection. This not only helps protect against malicious content but also aligns seamlessly with contemporary networking topologies like Software-Defined Wide Area Networks (SD-WAN) and zero-trust architectures.

















































Let's personalize your content