BrandPost: Firewalls: Severely Limited in DDoS Attack Protection
CSO Magazine
NOVEMBER 29, 2021
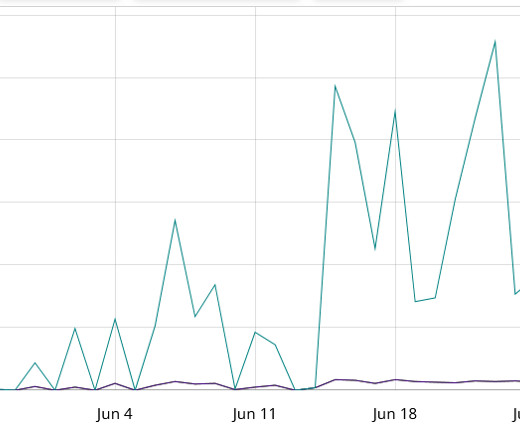
Many cybersecurity companies rely on devices such as firewalls, virtual private networks (VPNs), load balancers, and other edge devices to protect enterprise networks from distributed denial-of-service (DDoS) attacks. But the reality is that such devices contain “state” information that’s used for routing and traffic management.
















































Let's personalize your content