From Backup to Backdoor: Exploitation of CVE-2022-36537 in R1Soft Server Backup Manager
Fox IT
FEBRUARY 22, 2023
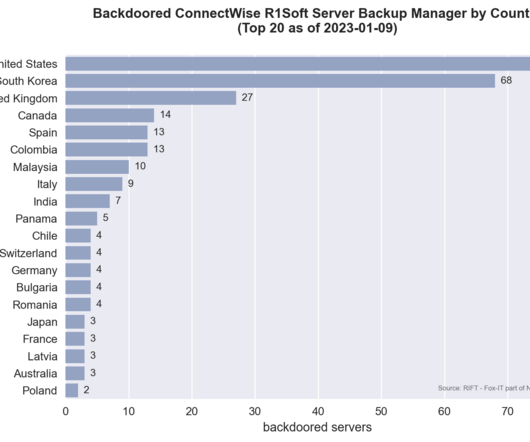
During a recent incident response case, we found traces of an adversary leveraging ConnectWise R1Soft Server Backup Manager software (hereinafter: R1Soft server software). The adversary used it as an initial point of access and as a platform to control downstream systems connected via the R1Soft Backup Agent.
















































Let's personalize your content