Cisco Confirms Data Breach, Hacked Files Leaked
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
Dark Reading
AUGUST 11, 2022
Ransomware gang gained access to the company's VPN in May by convincing an employee to accept a multifactor authentication (MFA) push notification.

IT Security Guru
OCTOBER 26, 2023
Enter Two-Factor Authentication, or 2FA for short. Here’s a shocking stat: according to the Verizon Data Breach Investigations Report , 81% of hacking-related breaches leverage either stolen or weak passwords. Always use VPN for your safety to protect your data from prying eyes. What Exactly is 2FA?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 16, 2024
The threat actor compromised network administrator credentials through the account of a former employee that was used to successfully authenticate to an internal virtual private network (VPN) access point. The threat actor likely obtained the employee’s account credentials from a third-party data breach.
Security Affairs
DECEMBER 26, 2023
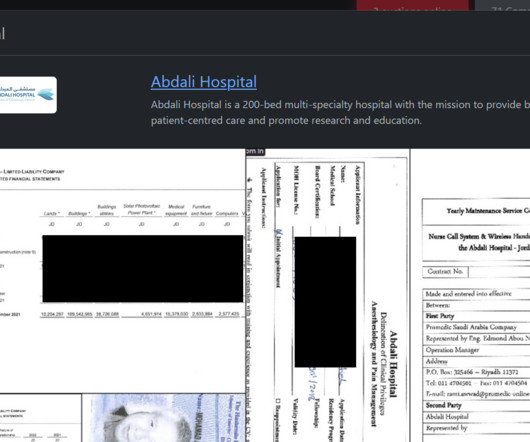
The Rhysida ransomware group claimed to have hacked Abdali Hospital, a multi-specialty hospital located in Jordan. pic.twitter.com/6uHMDcNhTC — Dominic Alvieri (@AlvieriD) December 26, 2023 The group published images of stolen documents as proof of the hack. Open your wallets and be ready to buy exclusive data.

Security Affairs
APRIL 28, 2024
From March 18, 2024, to April 16, 2024, Duo Security and Cisco Talos observed large-scale brute-force attacks against a variety of targets, including VPN services, web application authentication interfaces and SSH services.

Security Affairs
JULY 29, 2022
Therefore, strong authentication methods are needed. Therefore, strong authentication methods are needed to improve security without hindering user convenience. What is Strong Authentication? The IAM Security Boundary Strong authentication is a critical component of modern-day identity and access management.
Security Affairs
NOVEMBER 29, 2023
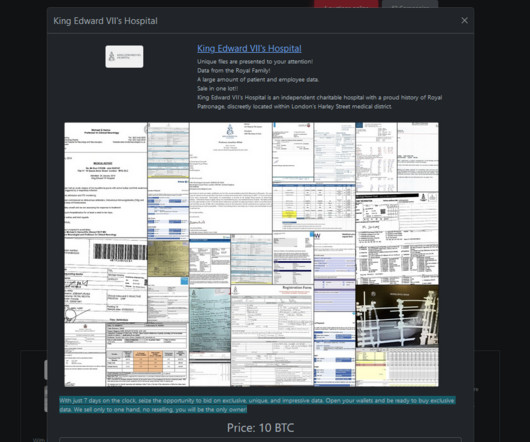
The Rhysida ransomware group claimed to have hacked King Edward VII’s Hospital in London. The Rhysida ransomware group claimed to have hacked King Edward VII’s Hospital in London and added it to the list of victims on its Tor leak site. King Edward VII’s Hospital in London has been breached by Rhysida Ransomware.

Security Affairs
JANUARY 13, 2024
Akira ransomware targets Finnish organizations GitLab fixed a critical zero-click account hijacking flaw Juniper Networks fixed a critical RCE bug in its firewalls and switches Vast Voter Data Leaks Cast Shadow Over Indonesia ’s 2024 Presidential Election Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467 Team Liquid’s wiki leak exposes (..)

Security Affairs
JANUARY 13, 2024
NAS (Network-Attached Storage) servers that are often used for backups on the network have been hacked and wiped, as have automatic tape backup devices, and in almost every case we know of, all backups have been lost. Cisco investigated the hacking campaign with the help of Rapid7. concludes the alert.

Security Affairs
OCTOBER 21, 2023
Okta says that threat actors broke into its support case management system and stole authentication data, including cookies and session tokens, that can be abused in future attacks to impersonate valide users. HAR files can also contain sensitive data, including authentication information. ” concludes the advisory.

Security Affairs
APRIL 12, 2019
At least four VPN apps sold or made available to enterprise customers share security flaws, warns the Carnegie Mellon University CERT Coordination Center (CERT/CC). Virtual private networks (VPNs) are affordable, easy to use, and a vital component in your system. What if these VPNs are vulnerable to attackers? 8.3R6, and 9.0R2.

Security Affairs
FEBRUARY 4, 2024
Clorox estimates the costs of the August cyberattack will exceed $49 Million Mastodon fixed a flaw that can allow the takeover of any account Iranian hackers breached Albania’s Institute of Statistics (INSTAT) Operation Synergia led to the arrest of 31 individuals Ex CIA employee Joshua Adam Schulte sentenced to 40 years in prison Cloudflare breached (..)

Security Affairs
JANUARY 13, 2024
NAS (Network-Attached Storage) servers that are often used for backups on the network have been hacked and wiped, as have automatic tape backup devices, and in almost every case we know of, all backups have been lost. Cisco investigated the hacking campaign with the help of Rapid7. concludes the alert.

The Last Watchdog
MARCH 6, 2021
Related: Poll confirms rise of Covid 19-related hacks. Set-up 2-factor authentication. If somehow passwords are leaked, a hacker can cause a data breach. Two-factor authentication or two-step verification involves adding a step to add an extra layer of protection to accounts. Use antivirus software.

Security Affairs
JULY 27, 2023
This would make it extremely complicated for the company to inform its clients about a data breach or to warn them of malware attacks,” researchers said. What DepositFiles data was exposed? The exposed file had credentials for the Redis database, allowing anyone to read, edit, or delete data stored there.

Adam Levin
NOVEMBER 15, 2019
News that Virtual Private Network ( VPN ) provider NordVPN was breached spread quickly. While the breach of a major VPN service is newsworthy, this one wasn’t particularly. But one of the watchwords of good cyber hygiene, a VPN, was breached. Who Is Using VPNs? SMB vs. Enterprise.

Krebs on Security
APRIL 6, 2022
Many organizations are already struggling to combat cybersecurity threats from ransomware purveyors and state-sponsored hacking groups, both of which tend to take days or weeks to pivot from an opportunistic malware infection to a full blown data breach. In fact, the group often announces its hacks on social media.

Security Affairs
JUNE 23, 2020
CLOP ransomware operators have allegedly hacked IndiaBulls Group , an Indian conglomerate headquartered in Gurgaon, India. CLOP ransomware operators have allegedly hacked the Indian conglomerate IndiaBulls Group , its primary businesses are housing finance, consumer finance, and wealth management. . Pierluigi Paganini.

Krebs on Security
MAY 19, 2020
In January 2019, dozens of media outlets raised the alarm about a new “megabreach” involving the release of some 773 million stolen usernames and passwords that was breathlessly labeled “the largest collection of stolen data in history.” For more on this dynamic, please see The Value of a Hacked Email Account.

Security Affairs
MAY 2, 2022
Data has become a well-nigh priceless commodity, the cause of a never-ending Armageddon war between those who safeguard our masses of data and those who want it for nefarious purposes. In this ongoing war, some types of data storage are more prone to hacking because of the need to access, process, and analyze data quickly.

Krebs on Security
OCTOBER 21, 2019
Antivirus and security giant Avast and virtual private networking (VPN) software provider NordVPN each today disclosed months-long network intrusions that — while otherwise unrelated — shared a common cause: Forgotten or unknown user accounts that granted remote access to internal systems with little more than a password.

Security Affairs
AUGUST 27, 2023
military procurement system Spoofing an Apple device and tricking users into sharing sensitive data Israel and US to Invest $3.85 military procurement system Spoofing an Apple device and tricking users into sharing sensitive data Israel and US to Invest $3.85 Korean Kimsuky APT targets S. Korean Kimsuky APT targets S.

Security Affairs
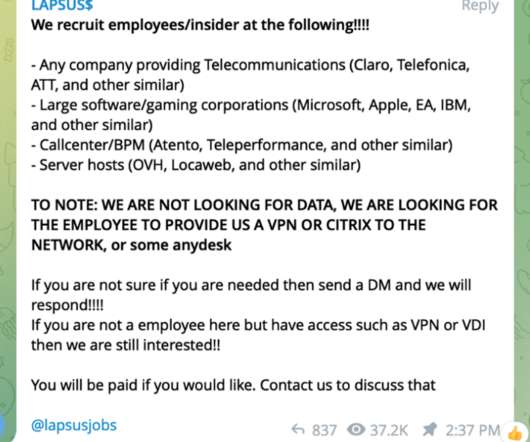
SEPTEMBER 12, 2022
Upon achieving an MFA push acceptance, the attacker had access to the VPN in the context of the targeted user. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user. . SecurityAffairs – hacking, Cisco). Pierluigi Paganini.
Krebs on Security
MARCH 23, 2022
For a fee, the willing accomplice must provide their credentials and approve the MFA prompt or have the user install AnyDesk or other remote management software on a corporate workstation allowing the actor to take control of an authenticated system. The group has claimed it is not state-sponsored.

Security Affairs
MAY 9, 2021
Experts found critical authentication bypass flaw in HPE Edgeline Infrastructure Manager UNC2529, a new sophisticated cybercrime gang that targets U.S. Experts found critical authentication bypass flaw in HPE Edgeline Infrastructure Manager UNC2529, a new sophisticated cybercrime gang that targets U.S. Pierluigi Paganini.

SecureWorld News
FEBRUARY 9, 2024
Gartner has projected that by 2025, more than 60% of organizations will move away from VPN and rely on ZTNA. RELATED: Death of the VPN: A Security Eulogy ] VPNs have notably higher operating costs and lower scalability when using device-based architecture. Enable data driven device registration.

Security Affairs
AUGUST 7, 2022
of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4 of its users due to the exposure of salted password hashes Twitter confirms zero-day used to access data of 5.4 SecurityAffairs – hacking, newsletter). Pierluigi Paganini.

IT Security Guru
MARCH 28, 2023
Having a cybersecurity plan ensures that you remain protected against data breaches, phishing scams , and other cybercrimes. On top of that, turn on two factor authentication. Use a VPN Using a VPN is essential when working with sensitive data or files.

Security Affairs
NOVEMBER 29, 2020
SecurityAffairs – hacking, newsletter). Pierluigi Paganini. The post Security Affairs newsletter Round 291 appeared first on Security Affairs.

CyberSecurity Insiders
DECEMBER 6, 2022
When employees aren’t in the office, they’re liable to engage in risky behaviors such as using unsecured WiFi without a VPN, leaving work devices unlocked in public places, and clicking on malicious emails. Companies should also provide clear channels for reporting suspicious incidents.
Security Affairs
MAY 11, 2023
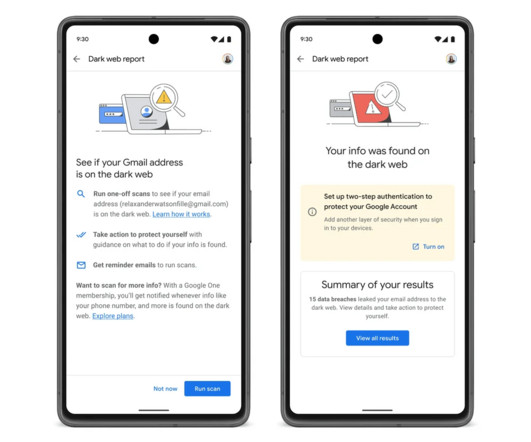
Once an email address is discovered on the dark web, Google will urge users to enable two-step authentication (2FA) to protect their Google accounts. Google also announced the availability of VPN access for all Google One plans. The upcoming feature will be also extended to users from select international markets. We are in the final!
Security Affairs
MARCH 23, 2022
Microsoft confirmed that Lapsus$ extortion group has hacked one of its employees to access and steal the source code of some projects. Microsoft confirmed that Lapsus$ extortion group has hacked one of its employees to access and steal the source code of some projects. SecurityAffairs – hacking, Microsoft). Pierluigi Paganini.

Krebs on Security
JULY 10, 2022
Twice in the past month KrebsOnSecurity has heard from readers who’ve had their accounts at big-three credit bureau Experian hacked and updated with a new email address that wasn’t theirs. “I was able to answer the credit report questions successfully, which authenticated me to their system,” Turner said.

CyberSecurity Insiders
DECEMBER 18, 2021
Use Strong Passwords & Two-Factor Authentication. If your password is exposed in a data breach, you must change it immediately. Websites might inform you via e-mail when such breaches occur, but with a considerable delay. Avoid reusing them across other websites, no matter how unimportant.

Webroot
FEBRUARY 15, 2024
If you’ve been compromised in a data breach, hackers can use your stolen email and password to try and enter thousands of other sites—and if you keep using the same credentials, they’ll be successful. Use two-factor authentication Two-factor authentication adds an extra layer of security to your online accounts.

Adam Levin
FEBRUARY 13, 2019
The data used in these attacks could be from different places. One six-month period last year resulted in 945 data breaches with a total of 4.5 The credentials used in stuffing exploits are acquired from a variety of sources, including black market repositories of data breach content. billion records compromised.
Security Affairs
APRIL 23, 2022
The VPN credentials for initial access are said to have been obtained from illicit websites like Russian Market with the goal of gaining control of T-Mobile employee accounts, ultimately allowing the threat actor to carry out SIM swapping attacks at will. SecurityAffairs – hacking, T-Mobile). ” wrote Krebs. Pierluigi Paganini.

Cisco Security
OCTOBER 20, 2022
According to Verizon’s Data Breach Investigations Report , 82% of breaches involve the human element — whether it’s stolen credentials, phishing, misuse or error. For example, with Cisco Secure Access by Duo, organizations can provide those connecting to their network with several quick, easy authentication options.
Security Affairs
SEPTEMBER 10, 2020
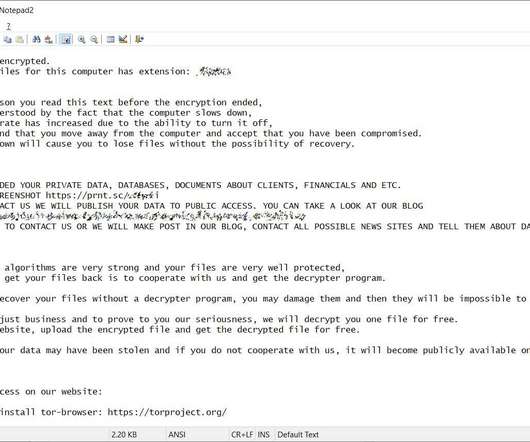
. “LOOK AT THIS SCREENSHOT [link] IF YOU NOT CONTACT US WE WILL PUBLISH YOUR DATA TO PUBLIC ACCESS. “The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation.” Consider installing and using a VPN.

Security Affairs
APRIL 3, 2022
Sophos Firewall affected by a critical authentication bypass flaw Mar 20- Mar 26 Ukraine – Russia the silent cyber conflict Security Affairs newsletter Round 358 by Pierluigi Paganini Western Digital addressed a critical bug in My Cloud OS 5 CISA adds 66 new flaws to the Known Exploited Vulnerabilities Catalog. Pierluigi Paganini.

CyberSecurity Insiders
SEPTEMBER 14, 2021
This does not bode well for their longevity, as other industry data shows that 60% of small businesses that suffer a data breach will be out of business within six months. Use of a VPN – virtual private networks (VPN) create a secure connection to other networks over the internet.

Thales Cloud Protection & Licensing
APRIL 9, 2020
With the high amount of cybercriminal activity including hacking attempts and phishing scams, the information in this report is quite timely. The bad actors also “leveraged usernames and passwords acquired in previous data breaches. Authentication assurance to the rescue! BEC is the costliest crime for businesses.

CyberSecurity Insiders
OCTOBER 29, 2021
A few simple changes to your devices and accounts can help discourage cyber criminals from trying to access your data. Prevent Data Breaches. Giants like Facebook and Target have suffered breaches and password leaks, so it’s safe to say data from at least one of your online accounts could have been leaked.

Malwarebytes
JUNE 3, 2022
Just last month, after the Twitter account of a famous digital artist was hacked, cybercriminals abused the account to send promotions for a fraudulent collaboration between the artist and the luxury brand Lous Vuitton. Do use two-factor (also called multi-factor) authentication. Do use a VPN on public WiFi connections.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content