Scammers can easily phish your multi-factor authentication codes. Here’s how to avoid it
Malwarebytes
MAY 16, 2024
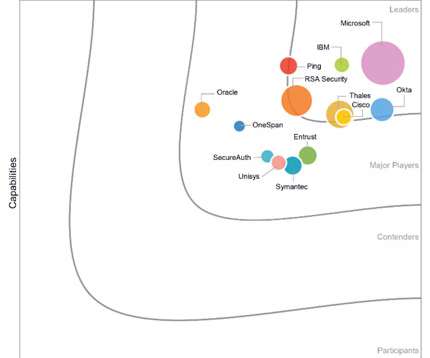
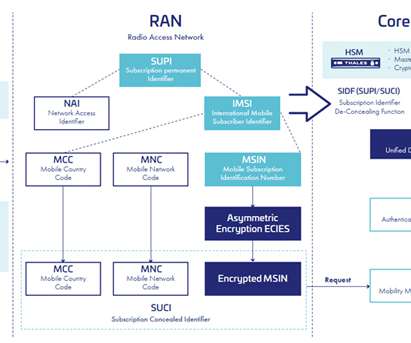
More and more websites and services are making multi-factor-authentication (MFA) mandatory, which makes it much harder for cybercriminals to access your accounts. A type of phishing we’re calling authentication-in-the-middle is showing up in online media. Keep threats off your devices by downloading Malwarebytes today.











































Let's personalize your content