A Threat to Passkeys? BrutePrint Attack Bypasses Fingerprint Authentication
eSecurity Planet
MAY 22, 2023
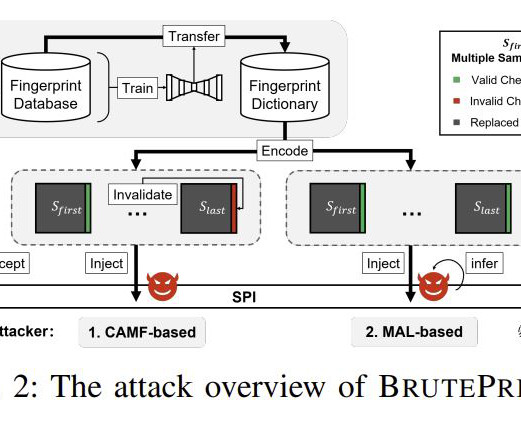
Security researchers recently published a paper detailing an attack they say can be used to bypass smartphone fingerprint authentication. An attack like BrutePrint could present a significant threat to passkeys , an increasingly popular way to replace passwords with authentication methods like fingerprint authentication or face recognition.

















































Let's personalize your content