Rorschach ransomware has the fastest file-encrypting routine to date
Security Affairs
APRIL 4, 2023
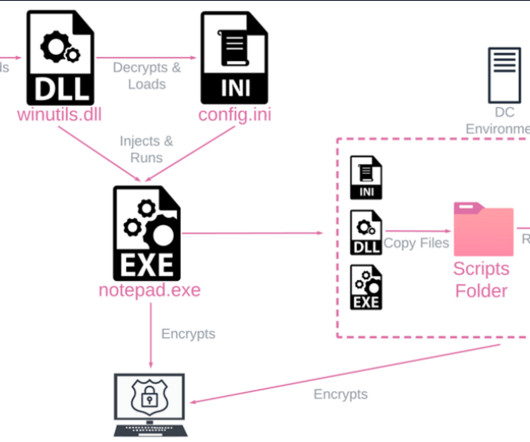
A new ransomware strain named Rorschach ransomware supports the fastest file-encrypting routine observed to date. The researchers conducted five separate encryption speed tests in a controlled environment (with 6 CPUs, 8192MB RAM, SSD, and 220000 files to be encrypted), limited to local drive encryption only.

































Let's personalize your content