What to do if you suspect your personal mobile has been hacked
BH Consulting
FEBRUARY 23, 2023
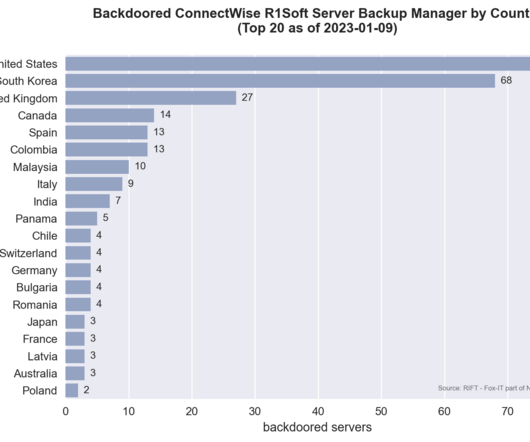
But what happens if you think your mobile has been breached? In this blog, we’ll look at how you can minimise the impact of your personal mobile being compromised. Check and protect what you value most Identify the important apps or files on your mobile phone. (Do Encrypt the data stored on your mobile phone.







































Let's personalize your content