How to recover files encrypted by Yanlouwang
SecureList
APRIL 18, 2022
Kaspersky experts have found a vulnerability in the Yanluowang encryption algorithm and created a free decryptor to help victims of this ransomware with recovering their files. This is necessary to make files used by other programs available for encryption. The encryption code for big files. Yanluowang description.






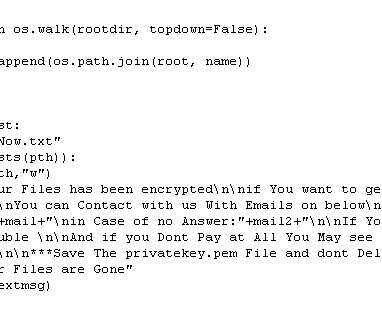











































Let's personalize your content