2023 Predictions for Storage and Backup Ransomware
CyberSecurity Insiders
JANUARY 6, 2023
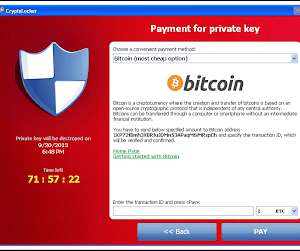
By Doron Pinhas, Chief Technology Officer, Continuity. Many of these attacks took advantage of known vulnerabilities and security misconfigurations in storage and backup systems. Many of these attacks took advantage of known vulnerabilities and security misconfigurations in storage and backup systems.





































Let's personalize your content