Iran-linked MERCURY APT behind destructive attacks on hybrid environments
Security Affairs
APRIL 10, 2023
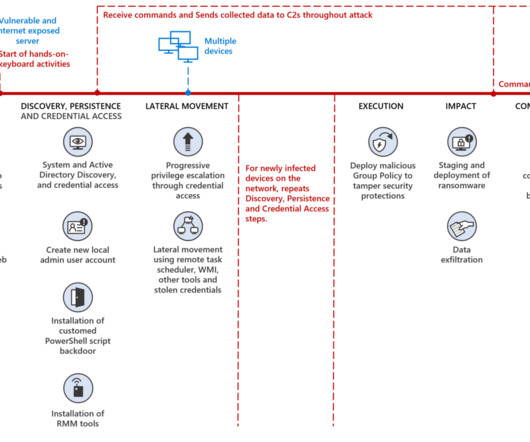
.” DEV-1084 presented itself as cybercrime group likely as an attempt to hide its real motivation of a nation-state actor. Both groups used MULLVAD VPN. The attackers were able to interfere with security tools using Group Policy Objects (GPO). DEV-1084 used Rport and a customized version of Ligolo.










Let's personalize your content