GUEST ESSAY: Why automating distribution of strong passwords to employees is wise to do
The Last Watchdog
APRIL 28, 2022
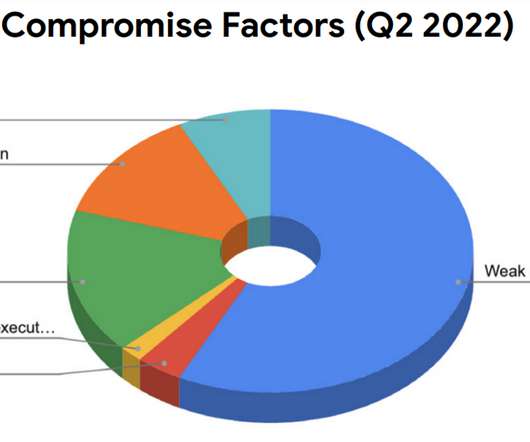
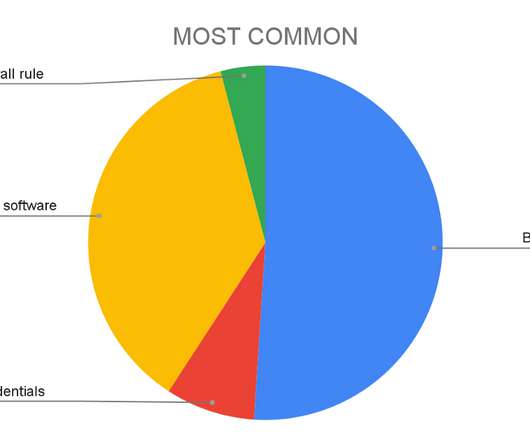
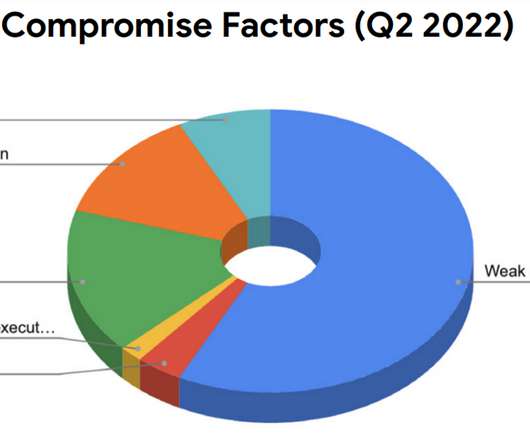
Passwords have become ubiquitous with digital. The humble password is nothing more than a digital key that opens a door. And they use passwords to open a device, a system, an account, a file and so on. Which begs the question: why do people create their own passwords? Yet most people don’t know how to use them properly.










































Let's personalize your content