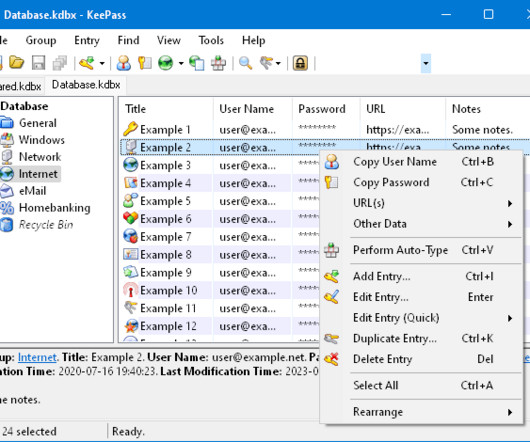
KeePass 2.X Master Password Dumper allows retrieving the KeePass master password
Security Affairs
MAY 18, 2023
A researcher published a PoC tool to retrieve the master password from KeePass by exploiting the CVE-2023-32784 vulnerability. X Master Password Dumper that allows retrieving the master password for KeePass. ” KeePass is a free and open-source software used to securely manage passwords. x versions. x versions.









































Let's personalize your content