Security Risks of Outdated Encryption
GlobalSign
DECEMBER 11, 2023
In this blog we will discuss how outdated encryption methods can be detrimental to businesses and explore proactive solutions.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
GlobalSign
DECEMBER 11, 2023
In this blog we will discuss how outdated encryption methods can be detrimental to businesses and explore proactive solutions.

GlobalSign
FEBRUARY 14, 2024
In this blog, we review why automation and encryption are important in improving time efficiency and mitigating risks in digital certificate management workflows.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
OCTOBER 15, 2021
The idea is that they wouldn’t touch the cryptography, but instead eavesdrop on communications and systems before encryption or after decryption. I’m part of a group of cryptographers that has just published a paper discussing the security risks of such a system. (It’s It means I don’t have to.)
Troy Hunt
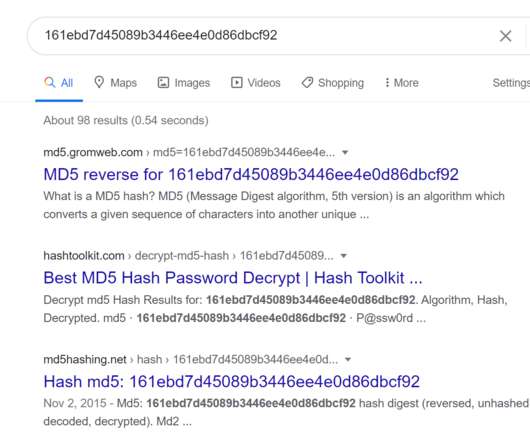
SEPTEMBER 3, 2020
The organisation involved may have contacted you and advised your password was exposed but fortunately, they encrypted it. Isn't the whole point of encryption that it protects data when exposed to unintended parties? This entire blog post hashed with Md5 is still 32 characters long. But you should change it anyway. With bcrypt.

The Last Watchdog
FEBRUARY 5, 2024
One critical issue faced by organizations that rely on Exchange Server is the risk of a corrupt Exchange Server database cropping up. Navigating new risks Today, heavy reliance on cloud-centric IT infrastructure and cloud-hosted applications has become the norm. Here are a few ‘dos:’ •Rigorous vulnerability management.

The Last Watchdog
AUGUST 29, 2023
Here’s what you should know about the risks, what aviation is doing to address those risks, and how to overcome them. It is difficult to deny that cyberthreats are a risk to planes. Risks delineated Still, there have been many other incidents since. Fortunately, there are ways to address the risks.

The Last Watchdog
JANUARY 10, 2022
Related: The dangers of normalizing encryption for government use. It’s possible to de-risk work scenarios involving personal data by carrying out a classic risk assessment of an organization’s internal and external infrastructure. This de-risks personal data that does not fit in a separate security contour. Encryption.

Thales Cloud Protection & Licensing
AUGUST 17, 2022
The value of Key Rotation and Re-encryption. To meet various compliance requirements and reduce the risk of your most sensitive data getting compromised you may want to consider changing the encryption key used to protect this data. Thales refers to this changing of encryption keys as “Key rotation” or “Rekey”.

Heimadal Security
NOVEMBER 21, 2022
It encrypts the files of victims and demands payment, but it also steals the Discord accounts of infected users—a double-edged sword. First, AXLocker encrypts your files. First, its potential risk is that […]. AXLocker is a new strain of ransomware discovered in late November 2022. How Does The Virus Work?

Thales Cloud Protection & Licensing
NOVEMBER 15, 2021
How encryption can help address Cloud misconfiguration. So, whichever way you go, there is, across time, a very high likelihood that a CSP's encryption, tokenization, or key management scheme will be misconfigured either by the CSP itself or by the CSP user. Bring your own encryption (BYOE). Tue, 11/16/2021 - 06:15.

Heimadal Security
MARCH 29, 2023
Hackers can use C&C or C2 servers to create botnets and launch DDoS attacks, steal, delete, and/or encrypt data. Techniques and DNS Security Risks appeared first on Heimdal Security Blog. Basically, a […] The post Command-and-Control Servers Explained.

Security Boulevard
MAY 23, 2023
Organizations are accelerating plans for data encryption, driven by increased security, privacy, and cloud workload protection requirements. However, there are a few different approaches to data encryption and enterprises must consider several factors before choosing the right tools and architecture for their needs.

Thales Cloud Protection & Licensing
MARCH 13, 2019
At the 2019 RSA Conference, Pure Storage and Thales introduced Vormetric Transparent Encryption for Efficient Storage – the IT and security industries’ first end-to-end data encryption framework that realizes storage array data reduction. Storage Costs of Encrypted Data.

CyberSecurity Insiders
MAY 28, 2023
However, as AI continues to advance, it brings with it a new set of cybersecurity risks and challenges. In this blog, we will delve into the potential risks associated with AI and the importance of implementing robust cybersecurity measures to safeguard against these threats.

Thales Cloud Protection & Licensing
APRIL 17, 2024
A Pandora's Box: Unpacking 5 Risks in Generative AI madhav Thu, 04/18/2024 - 05:07 Generative AI (GAI) is becoming increasingly crucial for business leaders due to its ability to fuel innovation, enhance personalization, automate content creation, augment creativity, and help teams explore new possibilities.

Centraleyes
FEBRUARY 25, 2024
However, critical security risks and threats inherent in cloud environments come alongside the myriad benefits. This blog aims to dissect the nuances of cloud security risks , shedding light on the challenges commonly faced when securing digital assets in the cloud. Who’s Responsible for Security in the Cloud?

Security Boulevard
APRIL 17, 2024
A Pandora's Box: Unpacking 5 Risks in Generative AI madhav Thu, 04/18/2024 - 05:07 Generative AI (GAI) is becoming increasingly crucial for business leaders due to its ability to fuel innovation, enhance personalization, automate content creation, augment creativity, and help teams explore new possibilities.

Centraleyes
JANUARY 18, 2024
A harmonious balance ensures that the organization benefits from the spark of innovation without succumbing to the risks that may accompany it. Relying too heavily on innovative but volatile partners may introduce unnecessary risks. Use a third-party risk assessment template to facilitate this task.

Centraleyes
APRIL 23, 2024
The digital landscape is advancing, and the risks of shirking cutting-edge technology are substantial. It’s well known that while new technologies open up novel pathways, they also come with risks. According to a recent Deloitte report , more than half (52%) of consumers feel more at risk in the digital environment.

Thales Cloud Protection & Licensing
NOVEMBER 24, 2020
Mitigating Ransomware Attacks – Decoupling Encryption Keys From Encrypted Data. Once the hackers gain an inside entry in an organisation’s IT systems, they deploy a file-encrypting malware known as ransomware. Some ransomware selectively seeks out sensitive data and will only encrypt those files. Wed, 11/25/2020 - 05:55.
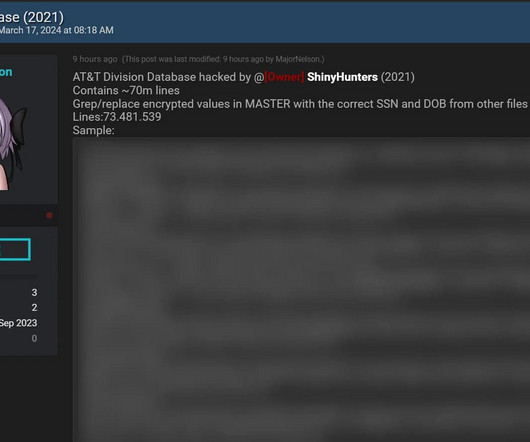
Troy Hunt
MARCH 18, 2024
I linked to the story from the beginning of this blog post and got a handful of willing respondents for whom I sent their data and asked two simple questions: Does this data look accurate? The above example simply didn't have plain text entries for the encrypted data.

Security Boulevard
MARCH 29, 2021
Sometimes great old blog posts are hard to find (especially on Medium …), so I decided to do a periodic list blog with my favorite posts of the past quarter or so. It covers both Anton on Security and my posts from Google Cloud blog [and now our Cloud Security Podcast too!]. Here is my second. Data Security and Threat Models”.

Thales Cloud Protection & Licensing
MAY 7, 2019
For many years, encryption has been viewed as a burden on businesses – expensive, complex and of questionable value. The 2019 Thales Data Threat Report-Global Edition revealed that as digital transformations are taking place, sensitive data is often at risk. Enter encryption. Originally published in TEISS on May 1, 2019.

CyberSecurity Insiders
FEBRUARY 1, 2022
This blog was written by an independent guest blogger. With quantum computing looming in the not-so-distant future, the way that we think about encryption will need to evolve. However, the complex math behind creating encryption keys is no match for the power of quantum computers. What are the security risks?

The Last Watchdog
MAY 5, 2022
Let’s walk through some practical steps organizations can take today, implementing zero trust and remote access strategies to help reduce ransomware risks: •Obvious, but difficult – get end users to stop clicking unknown links and visiting random websites that they know little about, an educational challenge. Best practices.

Security Boulevard
MAY 13, 2022
Types of Encryption Algorithms. How Do Encryption Algorithms Work? Encryption algorithms are mathematical formulas that transform plaintext into ciphertext. Put simply, algorithms make encrypting and decrypting code possible, specifically between the correct users. Types of Encryption. Symmetric Encryption.

The Last Watchdog
JANUARY 8, 2023
Smarter security to me broadly refers to relentlessly focusing on fundamentals while maturing the program, making sure your risk posture aligns with your business strategy. This means secure file transfer solutions, so you don’t waste time with slow encrypting protocols. This leads to revenue gains and positive customer outcomes.

Centraleyes
FEBRUARY 13, 2024
Categorizing risks as high, medium, or low has been the go-to method for organizations seeking to prioritize their cybersecurity efforts. Ten Risks in a Bed Remember the nursery rhyme? Enter the need for a more precise and actionable approach — Cyber Risk Quantification. What is Cyber Risk Quantification?

The Last Watchdog
MAY 31, 2024
Consequently, ensuring the security of these models has become a top priority to prevent potential risks and threats. Encrypting data during transmissionwill prevent unauthorized access. Storing training data in encrypted containers or secure databases adds a further layer of security. Data security. Model Security. Development.

Security Boulevard
JUNE 6, 2023
Telegram, a popular encrypted messaging app known for its commitment to privacy and security, has ironically become a hub for cybercriminal activities. The post Telegram Hacking Channels: An Emerging Risk appeared first on Security Boulevard.

Security Boulevard
MARCH 26, 2022
Open Source Sabotage and Encryption Efficacy Emerge as Tactics in Ukraine Resistance. The protestware event exposes some of the risks posed when armies of volunteer developers produce the code that’s crucial for hundreds or thousands of other applications to run,” Ars Technica said. Ukrainians get serious about encryption.

Thales Cloud Protection & Licensing
JANUARY 18, 2018
Enterprise risk managers continue to swing the pendulum between business risk and security risk, depending on new demands versus new threats. In lots of cases, enterprise risk teams have determined that the business risk of not leveraging the cloud far outweighs the inherent security risks of the cloud.

Thales Cloud Protection & Licensing
FEBRUARY 17, 2020
This presents a security risk to businesses. When it comes to data security, more organizations are tempted to use cloud native encryption and key management services because it’s simple and easily available. One issue is that cloud native encryption and key management services provide just basic data security.

Thales Cloud Protection & Licensing
MARCH 12, 2019
At the 2019 RSA Conference, Pure Storage and Thales introduced Vormetric Transparent Encryption for Efficient Storage – the IT and security industries’ first end-to-end data encryption framework that realizes storage array data reduction. Storage Costs of Encrypted Data.

Thales Cloud Protection & Licensing
MARCH 13, 2018
Data encryption has been around almost since the age of computers. In truth, anyone with minimal experience can write a simple script that uses default services built into virtually every OS to encrypt data. In Linux, for instance, it takes four openSSL commands to generate an encryption key and encrypt data.

Security Boulevard
JULY 7, 2022
Risks to Your Network from Insecure Code Signing Processes. However, this practice puts these critical resources at risk for being misused or compromised. However, this practice puts these critical resources at risk for being misused or compromised. brooke.crothers. Thu, 07/07/2022 - 15:26. Private key sprawl. Related Posts.

Thales Cloud Protection & Licensing
FEBRUARY 27, 2019
It turns out that enterprise companies diving head-first into digital transformation technologies are leaving their organizations open to unprecedented risk. These stunning results underscore the importance of enterprise organizations to encrypt sensitive data as part of their digital transformation strategy as opposed to an afterthought.

eSecurity Planet
AUGUST 5, 2021
The threat comes from three primary areas, they wrote: Supply chain risks (an attack vector that became a high-profile threat after the SolarWinds attack ), malicious threat actors and insider threats. It helps reduce risks through deep visibility into the host operating system and OpenShift and reports back metrics to reduce risk.

Anton on Security
OCTOBER 21, 2020
From Google Cloud Blog: “Improving security, compliance, and governance with cloud-based DLP data discovery” So, I’ve been doing some blogging at Google Cloud blog with most posts connected to products, launches, etc. However, I am also doing a fun blog series on DLP in the cloud. Blog 1 is here , and blog 2 is here? —?you

Anton on Security
FEBRUARY 26, 2021
The whole story from our GCP blog is cross-posted below: Security continues to be top of mind for large enterprises as well as smaller organizations and businesses. What risks are mitigated by confidential computing? How and where the data is encrypted? You can also download the episodes directly here. Follow @CloudSecPodcast.

Thales Cloud Protection & Licensing
FEBRUARY 7, 2019
So, what are we doing about encryption?”. Most alarmingly for enterprises, that risk will continue to rise– because the variety and severity of security risks will evolve. A spokesperson later added that this will focus on ensuring universal encryption of passport numbers. Tina Stewart, VP of Market Strategy. “So,

eSecurity Planet
JANUARY 11, 2024
When remote workers connect bring-your-own-device (BYOD) laptops, desktops, tablets, and phones to corporate assets, risk dramatically increases. These devices exist outside of direct corporate management and provide a ransomware gang with unchecked platforms for encrypting data. How does remote encryption work?

Security Boulevard
JANUARY 28, 2022
Compared to OTR (Off-the-Record) which basically allows single-user type of secure and encrypted communication the OMEMO protocol actually allows multi-user type of data and information exchange further strengthening the protocol's position on the market for secure mobile IM (instant messaging) applications. Stay tuned!

Thales Cloud Protection & Licensing
MARCH 10, 2021
Guest Blog: TalkingTrust. The problem becomes – how do we make sure we’re securing these “driving data centers” against the risks and threats that lurk on the Internet? The same rings true for encryption and authentication. due to weak encryption) allows hackers to gain authorized access to a vehicle.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content