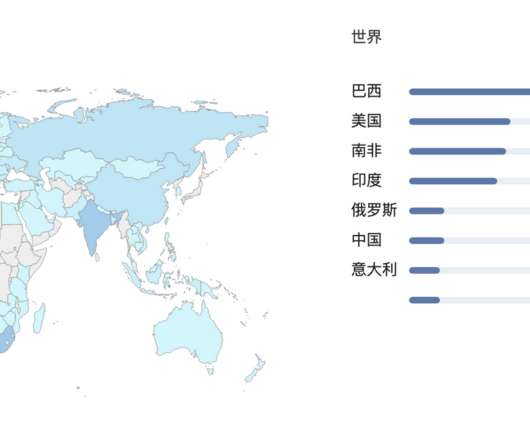
DDoS attacks in Q1 2021
SecureList
MAY 10, 2021
Botnet operators use infected devices to carry out DDoS attacks or mine cryptocurrency. In Q1 2021, cybercriminals also found a host of new tools for amplifying DDoS attacks. RDP servers listening on UDP port 3389 were used to amplify DDoS attacks. Alas, not all users of vulnerable programs and devices install updates promptly.



































Let's personalize your content