Beastmode Mirai botnet now includes exploits for Totolink routers
Security Affairs
APRIL 2, 2022
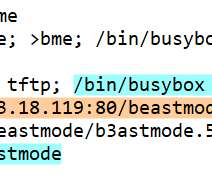
Operators behind the Mirai-based distributed denial-of-service (DDoS) botnet Beastmode (aka B3astmode) added exploits for Totolink routers. The Mirai -based distributed denial-of-service (DDoS) botnet Beastmode (aka B3astmode) now includes exploits for Totolink routers. SecurityAffairs – hacking, Beastmode botnet).















Let's personalize your content