Zero-Trust DNS
Schneier on Security
MAY 16, 2024
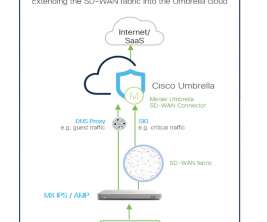
Microsoft is working on a promising-looking protocol to lock down DNS. ZTDNS aims to solve this decades-old problem by integrating the Windows DNS engine with the Windows Filtering Platform—the core component of the Windows Firewall—directly into client devices.














































Let's personalize your content