North Korea-linked Konni APT uses Russian-language weaponized documents
Security Affairs
NOVEMBER 24, 2023
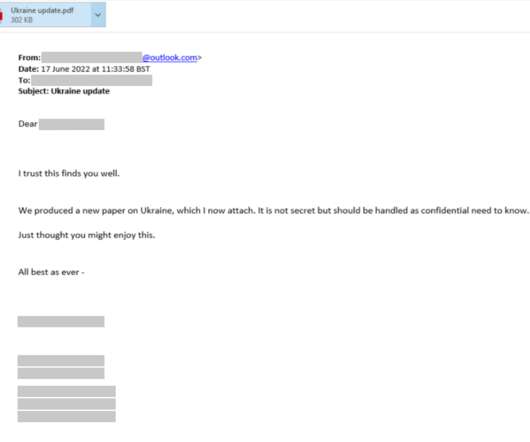
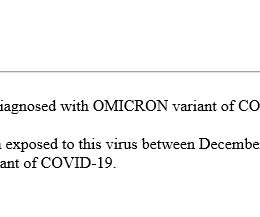
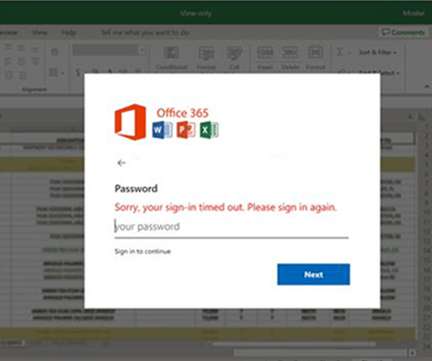
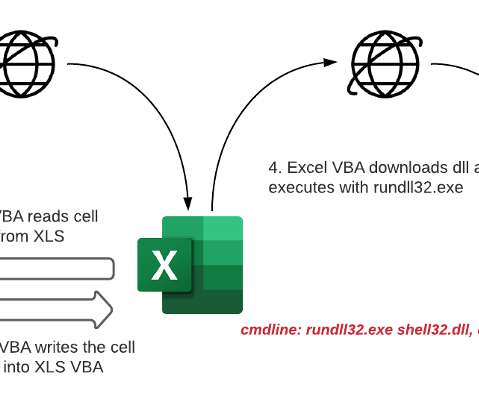
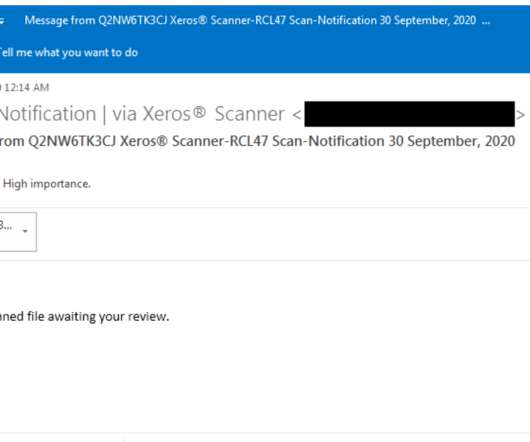
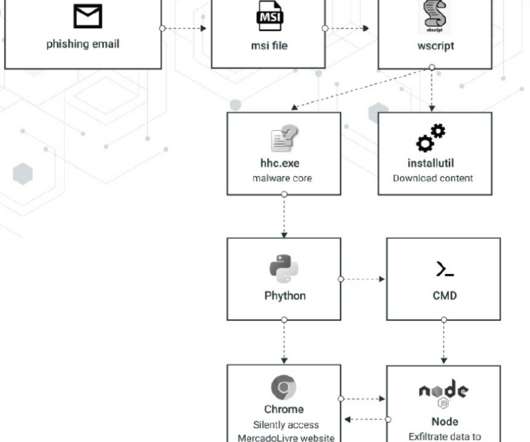
North Korea-linked Konni APT group used Russian-language Microsoft Word documents to deliver malware. FortiGuard Labs researchers observed the North Korea-linked Konni APT group using a weaponized Russian-language Word document in an ongoing phishing campaign. The Word document seems to be in the Russian language.























Let's personalize your content